CTF 질문 작성을 분석하는 방법
비교적 간단한 PWN 질문입니다. 먼저 그림과 같이 IDA로 끌어서 프로그램을 잠깐 살펴보세요.
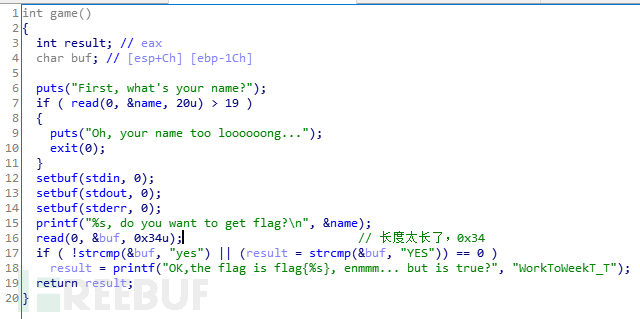
읽는 동안 스택 보호가 없는 것으로 나타났습니다. 0x34를 읽으면 게임 반환 주소, 첫 번째 패스 write(1,write,4)를 대체할 수 있습니다(게임은 쓰기 반환 주소로 사용됨). 이런 식으로 쓰기 주소를 읽으면 다시 루프에서 실행되고 0x804A06C에 /bin/sh를 쓰기 때문에 시스템 주소를 얻을 수 있습니다.
.replace("","").replace("r","").replace("n","").decode("hex")
dword_403018="""0200 00 00 02 00 00 00
0200 00 00 02 00 00 00 00 00 00 00 00 00 00 00
""".replace("","").replace("r","").replace("n"," ").decode("hex")
#text:0040110E 01113 mov dword_40301C, 3
#.text ; 403018= dword_ 403018[0:4] + 'x03' + dword_403018[5:8]
- 42):
hightnum= ord(dword_403018[ord(byte_402178[i])*4])
numbershow= hightnum+ ord(byte_402138[ord(var_6c[i])*4])
printchr(numbershow) ,
flag {06b16a72-51cc-4310-88ab-70ab68290e22}
0x03 sqli
이 질문은 SQL 제약 공격입니다. 등록된 사용자 이름은 "admin"이고 비밀번호는 규정에 맞는 비밀번호입니다. 그러면 플래그
flag {b5a1f9c5-ac30-4e88-b460-e90bcb65bd70}
0x04 RSA
opensslrsa -inform PEM -in pubkey1.pem -pubin -text
Public-Key:(2048 비트)가 표시됩니다.
모듈러스:
00:89: 89:a3:98:98:84:56:b3:fe:f4:a6:ad:86:df:
3c:99:57:7f:89:78: 04:8d:e5:43:6b: ef:c3:0d:8d:
8c:94:95:89:12:aa:52:6f:f3:33:b6:68:57:30:6e:
bb:8d:e3:6c: 2c:39:6a:84:ef:dc:5d:38:25:02:da:
a1:a3:f3:b6:e9:75:02:d2: e3:1c:84:93:30: f5:b4:
c9:52:57:a1:49:a9:7f:59:54:ea:f8:93:41:14:7a:
dc: dd:4e:95:0f:ff: 74:e3:0b:be:62:28:76:b4:2e:
ea:c8:6d:f4:ad:97:15:d0:5b:56: 04:aa:81:79:42:
4c:7d:9a:c4:6b:d6:b5:f3:22:b2:b5:72:8b:a1:48:
70:4a:25: a8:ef:cc:1e:7c: 84:ea:7e:5c:e3:e0:17:
03:f0:4f:94:a4:31:d9:95:4b:d7:ae:2c: 7d:d6:e8:
79: b3:5f:8a:2d:4a:5e:fb:e7:37:25:7b:f9:9b:d9:
ee:66:b1:5a:ff: 23:3f:c7:7b:55: 8a:48:7d:a5:95:
2f:be:2b:92:3d:a9:c5:eb:46:78:8c:05:03:36: b7:
e3:6a:5e: d8:2d:5c:1b:2a:eb:0e:45:be:e4:05:cb:
e7:24:81:db:25:68:aa: 82:9e:ea:c8:7d: 20:1a:5a:
8f:f5:ee:6f:0b:e3:81:92:ab:28:39:63:5f:6c:66:
42:17
지수:2333 (0x91d )
opensslrsa -inform PEM -in pubkey2.pem -pubin -text
공개 키:(2048비트)
모듈러스:
00:89:89:a3: 98:98:84:56:b3: fe:f4:a6:ad:86:df:
3c:99:57:7f:89:78:04:8d:e5:43:6b:ef:c3: 0d:8d:
8c:94: 95:89:12:aa:52:6f:f3:33:b6:68:57:30:6e:
bb:8d:e3:6c:2c:39: 6a:84:ef:dc:5d: 38:25:02:da:
a1:a3:f3:b6:e9:75:02:d2:e3:1c:84:93:30:f5:b4:
c9:52:57:a1: 49:a9:7f:59:54:ea:f8:93:41:14:7a:
dc:dd:4e:95:0f:ff:74:e3: 0b:be:62:28:76: b4:2e:
ea:c8:6d:f4:ad:97:15:d0:5b:56:04:aa:81:79:42:
4c: 7d:9a:c4:6b:d6: b5:f3:22:b2:b5:72:8b:a1:48:
70:4a:25:a8:ef:cc:1e:7c:84:ea: 7e:5c:e3:e0:17:
03:f0:4f:94:a4:31:d9:95:4b:d7:ae:2c:7d:d6:e8:
79:b3:5f: 8a:2d:4a:5e:fb: e7:37:25:7b:f9:9b:d9:
ee:66:b1:5a:ff:23:3f:c7:7b:55:8a:48: 7d:a5:95:
2f: be:2b:92:3d:a9:c5:eb:46:78:8c:05:03:36:b7:
e3:6a:5e:d8:2d: 5c:1b:2a:eb:0e: 45:be:e4:05:cb:
e7:24:81:db:25:68:aa:82:9e:ea:c8:7d:20:1a: 5a:
8f:f5:ee: 6f:0b:e3:81:92:ab:28:39:63:5f:6c:66:
42:17
지수:23333 (0x5b25).
이 두 공개 키 n은 동일함을 알 수 있습니다. 유일한 차이점은 RSA
Python을 사용한 공통 모드 공격은 다음과 같습니다.
fromlibnum import n2s,s2n
fromgmpy2 import invert
importbase64
importgmpy2
defbignumber(n):
n= n.decode( "hex")
rn= 0
forb in n:
rn= rn
rn+= ord(b)
returnrn
n ="""00:89:89:a 3 :98:98:84:56:b3:fe:f4:a6:ad:86:df:
3c:99:57:7f:89: 78:04:8d:e5:43:6b:ef:c3 :0d:8d:
8c:94:95:89:12:aa:52:6f:f3:33:b6:68:57:30: 6e:
bb:8d:e3:6c:2c:39:6a:84:ef:dc:5d:38:25:02:da:
a1:a3:f3:b6:e9:75:02:d2:e3 :1c:84:93:30:f5:b4:
c9:52:57:a1:49:a9:7f:59:54:ea:f8:93:41:14:7a:
dc:dd :4e:95:0f:ff:74:e3:0b:be:62:28:76:b4:2e:
ea:c8:6d:f4:ad:97:15:d0:5b:56:04 :aa:81:79:42:
4c:7d:9a:c4:6b:d6:b5:f3:22:b2:b5:72:8b:a1:48:
70:4a:25:a8 :ef:cc:1e:7c:84:ea:7e:5c:e3:e0:17:
03:f0:4f:94:a4:31:d9:95:4b:d7:ae:2c:7d :d6:e8:
79:b3:5f:8a:2d:4a:5e:fb:e7:37:25:7b:f9:9b:d9:
ee:66:b1:5a:ff:23 :3f:c7:7b:55:8a:48:7d:a5:95:
2f:be:2b:92:3d:a9:c5:eb:46:78:8c:05:03:36:b7 :
e3:6a:5e:d8:2d:5c:1b:2a:eb:0e:45:be:e4:05:cb:
e7:24:81:db:25:68:aa:82 :9e:ea:c8:7d:20:1a:5a:
8f:f5:ee:6f:0b:e3:81:92:ab:28:39:63:5f:6c:66:42:17 ""
.replace(":",").replace("",").replace("r","").replace("n","")
#printn
n =큰 숫자 (n) inprinthex (n)
e1 = 2333
e2 = 23333
defegcd (a, b) :
ifa == 0 :
return (b, 0,1)
:
g,y,x= egcd(b%a,a)
return(g,x - (b //a)*y,y)
flag1 = base64.b64decode(open("flag1.enc", "rb").read())
flag2 = base64.b64decode(open("flag2.enc","rb").read())
c1= s2n(flag1)
c2= s2n(flag2)
c2= 반전(c2,n)
#s= egcd(e1,e2)
#prints
s =gmpy2.gcdext(e1,e2)
#prints
s1= s[ 1]
s2= 0 - s[2]
prints1
prints2
m =pow(c1,s1,n) * pow(c2,s2,n)%n
printn2s(m)
flag {4b0b4c8a- 82f3-4d80-902b-8e7a5706f8fe}
0x05 抛砖引玉
1.根据CMS版本,在wooyun镜到漏洞细节,
网站存在注入,但是数据库用户表为空,另외发现发现文件下载漏洞,
down.php?urls=data/../config.php
下载文件发现DB_user/mvoa용户적密码
define('DB_PWD','B!hpp3Dn1.');
flag值: B !hpp3Dn1.
2.http://url/www.zip,获得网站备份文件,在config.php发现DB_user/root用户的密码
define('DB_PWD','mypasswd');
flag值:mypasswd
0x06 暗島陈仓
1.发现下载路径
/u-are-admin/download.php?dl=
显示文件找不到(u-A re-Admin/u-upload-file文件夹) ,发现关键目录/u-Are-Admin/
flag值:/u-Are-Admin/
2.재/u-Are-Admin/目录,可以上传文件,上传Php(大小写绕过)一句다운로드: Hacked356
3.shell能够直接查看超级管理员用户桌face根目录admin.txt文件的内容
flag值:ad16a159581c7085c771f
0x07 ›后台管理员明文密码,serverlog
flag值:serverlog
2 rootserver
flag值:rootserver
3.根目录password.txt内容
/classes/downloadfile.php?file=../../../../../../password.txt
플래그 值: c9c35cf409344312146fa7546a94d1a6
0x08 偷梁换柱
1.AWVS扫到./git源码泄露, 工具GitHack下载所有源码,현재据库文件发现用户name ,密码(adminAdmin@pgsql)
flag值:Admin@pgsql
2. 응용 프로그램 이름 密码登录, 管理图文可以上传一句话木马의 사진,
/admin/uploads/111.php.png
直接菜刀链接,png也能当成php直接https://tmp/access.log적内容的前16位
0x09 反客为主
1. https://www.sjk- uploads/UareHack.txt
密码是a,拿到shell可以获取phpStudy目录下Documents.txt의 内容
2.拿到shell可以获取ichunqiu사용户Desktop根目录password.txt적内容
3.getshell后,传msf木马无法反弹,最后使用QuarksPwDump拿到了ichunqi 당신이 사용하는 해시는 다음과 같습니다: 4ffe895918a454ce0f872dad8af0b4da:::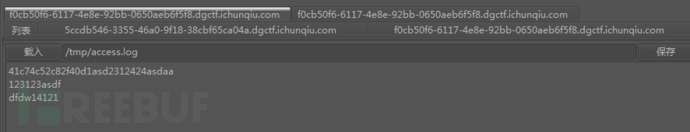
flag值:123qwe123
위 내용은 CTF 질문 작성을 분석하는 방법의 상세 내용입니다. 자세한 내용은 PHP 중국어 웹사이트의 기타 관련 기사를 참조하세요!

핫 AI 도구

Undresser.AI Undress
사실적인 누드 사진을 만들기 위한 AI 기반 앱

AI Clothes Remover
사진에서 옷을 제거하는 온라인 AI 도구입니다.

Undress AI Tool
무료로 이미지를 벗다

Clothoff.io
AI 옷 제거제

Video Face Swap
완전히 무료인 AI 얼굴 교환 도구를 사용하여 모든 비디오의 얼굴을 쉽게 바꾸세요!

인기 기사

뜨거운 도구

메모장++7.3.1
사용하기 쉬운 무료 코드 편집기

SublimeText3 중국어 버전
중국어 버전, 사용하기 매우 쉽습니다.

스튜디오 13.0.1 보내기
강력한 PHP 통합 개발 환경

드림위버 CS6
시각적 웹 개발 도구

SublimeText3 Mac 버전
신 수준의 코드 편집 소프트웨어(SublimeText3)

뜨거운 주제
 7728
7728
 15
15
 1643
1643
 14
14
 1397
1397
 52
52
 1290
1290
 25
25
 1233
1233
 29
29


