微信开发之消息体签名和加解密
前几篇主要是微信开发的准备工作,也没有什么技术含量。在第一篇和第二篇中,我主要讲的是使用花生壳来配合vs进行代码调试,也一度被园友吐槽本人是花生壳请来的逗比,没办法,为了和花生壳划清界限,在本篇进入正文前,为大家介绍一个比花生壳更好用的工具ngrok,ngrok的好处我就不在此具体说明了,毕竟不是本文的重点
出于安全考虑,微信公众平台在10月份的时候加入了消息体的加解密功能,首先,需要先验证签名,用于公众平台和公众账号验证消息体的正确性,其次,针对推送给公众号的普通消息和事件消息,以及推送给设备公众账号的设备进行加密,最后,公众号对密文消息的回复也需要加密。启用加解密功能后,公众平台服务器在向公众号服务器配置地址推送消息时,url将新增加两个参数,一个是加密类型一个是消息体签名,并以此来体现新功能。加密算法采用AES。关于明文模式,兼容模式,安全模式的说明,大家请参考官方文档.
验证消息真实性和加解密的帮助类官方提供的有demo,再次不详细讲述了,下载下来可以直接调用,下面请看代码:
using System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Security.Cryptography;using System.IO;using System.Net;namespace WxApi
{ public class Cryptography
{ public static UInt32 HostToNetworkOrder(UInt32 inval)
{
UInt32 outval = 0; for (int i = 0; i < 4; i++)
outval = (outval << 8) + ((inval >> (i * 8)) & 255); return outval;
} public static Int32 HostToNetworkOrder(Int32 inval)
{
Int32 outval = 0; for (int i = 0; i < 4; i++)
outval = (outval << 8) + ((inval >> (i * 8)) & 255); return outval;
} /// <summary>
/// 解密方法 /// </summary>
/// <param name="Input">密文</param>
/// <param name="EncodingAESKey"></param>
/// <returns></returns>
///
public static string AES_decrypt(String Input, string EncodingAESKey, ref string appid)
{ byte[] Key;
Key = Convert.FromBase64String(EncodingAESKey + "="); byte[] Iv = new byte[16];
Array.Copy(Key, Iv, 16); byte[] btmpMsg = AES_decrypt(Input, Iv, Key); int len = BitConverter.ToInt32(btmpMsg, 16);
len = IPAddress.NetworkToHostOrder(len); byte[] bMsg = new byte[len]; byte[] bAppid = new byte[btmpMsg.Length - 20 - len];
Array.Copy(btmpMsg, 20, bMsg, 0, len);
Array.Copy(btmpMsg, 20 + len, bAppid, 0, btmpMsg.Length - 20 - len); string oriMsg = Encoding.UTF8.GetString(bMsg);
appid = Encoding.UTF8.GetString(bAppid); return oriMsg;
} public static String AES_encrypt(String Input, string EncodingAESKey, string appid)
{ byte[] Key;
Key = Convert.FromBase64String(EncodingAESKey + "="); byte[] Iv = new byte[16];
Array.Copy(Key, Iv, 16); string Randcode = CreateRandCode(16); byte[] bRand = Encoding.UTF8.GetBytes(Randcode); byte[] bAppid = Encoding.UTF8.GetBytes(appid); byte[] btmpMsg = Encoding.UTF8.GetBytes(Input); byte[] bMsgLen = BitConverter.GetBytes(HostToNetworkOrder(btmpMsg.Length)); byte[] bMsg = new byte[bRand.Length + bMsgLen.Length + bAppid.Length + btmpMsg.Length];
Array.Copy(bRand, bMsg, bRand.Length);
Array.Copy(bMsgLen, 0, bMsg, bRand.Length, bMsgLen.Length);
Array.Copy(btmpMsg, 0, bMsg, bRand.Length + bMsgLen.Length, btmpMsg.Length);
Array.Copy(bAppid, 0, bMsg, bRand.Length + bMsgLen.Length + btmpMsg.Length, bAppid.Length); return AES_encrypt(bMsg, Iv, Key);
} private static string CreateRandCode(int codeLen)
{ string codeSerial = "2,3,4,5,6,7,a,c,d,e,f,h,i,j,k,m,n,p,r,s,t,A,C,D,E,F,G,H,J,K,M,N,P,Q,R,S,U,V,W,X,Y,Z"; if (codeLen == 0)
{
codeLen = 16;
} string[] arr = codeSerial.Split(','); string code = ""; int randValue = -1;
Random rand = new Random(unchecked((int)DateTime.Now.Ticks)); for (int i = 0; i < codeLen; i++)
{
randValue = rand.Next(0, arr.Length - 1);
code += arr[randValue];
} return code;
} private static String AES_encrypt(String Input, byte[] Iv, byte[] Key)
{ var aes = new RijndaelManaged(); //秘钥的大小,以位为单位
aes.KeySize = 256; //支持的块大小
aes.BlockSize = 128; //填充模式
aes.Padding = PaddingMode.PKCS7;
aes.Mode = CipherMode.CBC;
aes.Key = Key;
aes.IV = Iv; var encrypt = aes.CreateEncryptor(aes.Key, aes.IV); byte[] xBuff = null; using (var ms = new MemoryStream())
{ using (var cs = new CryptoStream(ms, encrypt, CryptoStreamMode.Write))
{ byte[] xXml = Encoding.UTF8.GetBytes(Input);
cs.Write(xXml, 0, xXml.Length);
}
xBuff = ms.ToArray();
}
String Output = Convert.ToBase64String(xBuff); return Output;
} private static String AES_encrypt(byte[] Input, byte[] Iv, byte[] Key)
{ var aes = new RijndaelManaged(); //秘钥的大小,以位为单位
aes.KeySize = 256; //支持的块大小
aes.BlockSize = 128; //填充模式 //aes.Padding = PaddingMode.PKCS7;
aes.Padding = PaddingMode.None;
aes.Mode = CipherMode.CBC;
aes.Key = Key;
aes.IV = Iv; var encrypt = aes.CreateEncryptor(aes.Key, aes.IV); byte[] xBuff = null; #region 自己进行PKCS7补位,用系统自己带的不行 byte[] msg = new byte[Input.Length + 32 - Input.Length % 32];
Array.Copy(Input, msg, Input.Length); byte[] pad = KCS7Encoder(Input.Length);
Array.Copy(pad, 0, msg, Input.Length, pad.Length); #endregion
#region 注释的也是一种方法,效果一样 //ICryptoTransform transform = aes.CreateEncryptor(); //byte[] xBuff = transform.TransformFinalBlock(msg, 0, msg.Length);
#endregion
using (var ms = new MemoryStream())
{ using (var cs = new CryptoStream(ms, encrypt, CryptoStreamMode.Write))
{
cs.Write(msg, 0, msg.Length);
}
xBuff = ms.ToArray();
}
String Output = Convert.ToBase64String(xBuff); return Output;
} private static byte[] KCS7Encoder(int text_length)
{ int block_size = 32; // 计算需要填充的位数
int amount_to_pad = block_size - (text_length % block_size); if (amount_to_pad == 0)
{
amount_to_pad = block_size;
} // 获得补位所用的字符
char pad_chr = chr(amount_to_pad); string tmp = ""; for (int index = 0; index < amount_to_pad; index++)
{
tmp += pad_chr;
} return Encoding.UTF8.GetBytes(tmp);
} /**
* 将数字转化成ASCII码对应的字符,用于对明文进行补码
*
* @param a 需要转化的数字
* @return 转化得到的字符 */
static char chr(int a)
{ byte target = (byte)(a & 0xFF); return (char)target;
} private static byte[] AES_decrypt(String Input, byte[] Iv, byte[] Key)
{
RijndaelManaged aes = new RijndaelManaged();
aes.KeySize = 256;
aes.BlockSize = 128;
aes.Mode = CipherMode.CBC;
aes.Padding = PaddingMode.None;
aes.Key = Key;
aes.IV = Iv; var decrypt = aes.CreateDecryptor(aes.Key, aes.IV); byte[] xBuff = null; using (var ms = new MemoryStream())
{ using (var cs = new CryptoStream(ms, decrypt, CryptoStreamMode.Write))
{ byte[] xXml = Convert.FromBase64String(Input); byte[] msg = new byte[xXml.Length + 32 - xXml.Length % 32];
Array.Copy(xXml, msg, xXml.Length);
cs.Write(xXml, 0, xXml.Length);
}
xBuff = decode2(ms.ToArray());
} return xBuff;
} private static byte[] decode2(byte[] decrypted)
{ int pad = (int)decrypted[decrypted.Length - 1]; if (pad < 1 || pad > 32)
{
pad = 0;
} byte[] res = new byte[decrypted.Length - pad];
Array.Copy(decrypted, 0, res, 0, decrypted.Length - pad); return res;
}
}
}using System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Xml;using System.Collections;//using System.Web;using System.Security.Cryptography;//-40001 : 签名验证错误//-40002 : xml解析失败//-40003 : sha加密生成签名失败//-40004 : AESKey 非法//-40005 : appid 校验错误//-40006 : AES 加密失败//-40007 : AES 解密失败//-40008 : 解密后得到的buffer非法//-40009 : base64加密异常//-40010 : base64解密异常namespace WxApi
{ public class MsgCrypt
{ string m_sToken; string m_sEncodingAESKey; string m_sAppID; enum WXBizMsgCryptErrorCode
{
WXBizMsgCrypt_OK = 0,
WXBizMsgCrypt_ValidateSignature_Error = -40001,
WXBizMsgCrypt_ParseXml_Error = -40002,
WXBizMsgCrypt_ComputeSignature_Error = -40003,
WXBizMsgCrypt_IllegalAesKey = -40004,
WXBizMsgCrypt_ValidateAppid_Error = -40005,
WXBizMsgCrypt_EncryptAES_Error = -40006,
WXBizMsgCrypt_DecryptAES_Error = -40007,
WXBizMsgCrypt_IllegalBuffer = -40008,
WXBizMsgCrypt_EncodeBase64_Error = -40009,
WXBizMsgCrypt_DecodeBase64_Error = -40010
}; //构造函数 // @param sToken: 公众平台上,开发者设置的Token // @param sEncodingAESKey: 公众平台上,开发者设置的EncodingAESKey // @param sAppID: 公众帐号的appid
public MsgCrypt(string sToken, string sEncodingAESKey, string sAppID)
{
m_sToken = sToken;
m_sAppID = sAppID;
m_sEncodingAESKey = sEncodingAESKey;
} // 检验消息的真实性,并且获取解密后的明文 // @param sMsgSignature: 签名串,对应URL参数的msg_signature // @param sTimeStamp: 时间戳,对应URL参数的timestamp // @param sNonce: 随机串,对应URL参数的nonce // @param sPostData: 密文,对应POST请求的数据 // @param sMsg: 解密后的原文,当return返回0时有效 // @return: 成功0,失败返回对应的错误码
public int DecryptMsg(string sMsgSignature, string sTimeStamp, string sNonce, string sPostData, ref string sMsg)
{ if (m_sEncodingAESKey.Length != 43)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_IllegalAesKey;
}
XmlDocument doc = new XmlDocument();
XmlNode root; string sEncryptMsg; try
{
doc.LoadXml(sPostData);
root = doc.FirstChild;
sEncryptMsg = root["Encrypt"].InnerText;
} catch (Exception)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_ParseXml_Error;
} //verify signature
int ret = 0;
ret = VerifySignature(m_sToken, sTimeStamp, sNonce, sEncryptMsg, sMsgSignature); if (ret != 0) return ret; //decrypt
string cpid = ""; try
{
sMsg = Cryptography.AES_decrypt(sEncryptMsg, m_sEncodingAESKey, ref cpid);
} catch (FormatException)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_DecodeBase64_Error;
} catch (Exception)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_DecryptAES_Error;
} if (cpid != m_sAppID) return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_ValidateAppid_Error; return 0;
} //将企业号回复用户的消息加密打包 // @param sReplyMsg: 企业号待回复用户的消息,xml格式的字符串 // @param sTimeStamp: 时间戳,可以自己生成,也可以用URL参数的timestamp // @param sNonce: 随机串,可以自己生成,也可以用URL参数的nonce // @param sEncryptMsg: 加密后的可以直接回复用户的密文,包括msg_signature, timestamp, nonce, encrypt的xml格式的字符串, // 当return返回0时有效 // return:成功0,失败返回对应的错误码
public int EncryptMsg(string sReplyMsg, string sTimeStamp, string sNonce, ref string sEncryptMsg)
{ if (m_sEncodingAESKey.Length != 43)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_IllegalAesKey;
} string raw = ""; try
{
raw = Cryptography.AES_encrypt(sReplyMsg, m_sEncodingAESKey, m_sAppID);
} catch (Exception)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_EncryptAES_Error;
} string MsgSigature = ""; int ret = 0;
ret = GenarateSinature(m_sToken, sTimeStamp, sNonce, raw, ref MsgSigature); if (0 != ret) return ret;
sEncryptMsg = ""; string EncryptLabelHead = "<Encrypt><![CDATA["; string EncryptLabelTail = "]]></Encrypt>"; string MsgSigLabelHead = "<MsgSignature><![CDATA["; string MsgSigLabelTail = "]]></MsgSignature>"; string TimeStampLabelHead = "<TimeStamp><![CDATA["; string TimeStampLabelTail = "]]></TimeStamp>"; string NonceLabelHead = "<Nonce><![CDATA["; string NonceLabelTail = "]]></Nonce>";
sEncryptMsg = sEncryptMsg + "<xml>" + EncryptLabelHead + raw + EncryptLabelTail;
sEncryptMsg = sEncryptMsg + MsgSigLabelHead + MsgSigature + MsgSigLabelTail;
sEncryptMsg = sEncryptMsg + TimeStampLabelHead + sTimeStamp + TimeStampLabelTail;
sEncryptMsg = sEncryptMsg + NonceLabelHead + sNonce + NonceLabelTail;
sEncryptMsg += "</xml>"; return 0;
} public class DictionarySort : System.Collections.IComparer
{ public int Compare(object oLeft, object oRight)
{ string sLeft = oLeft as string; string sRight = oRight as string; int iLeftLength = sLeft.Length; int iRightLength = sRight.Length; int index = 0; while (index < iLeftLength && index < iRightLength)
{ if (sLeft[index] < sRight[index]) return -1; else if (sLeft[index] > sRight[index]) return 1; else
index++;
} return iLeftLength - iRightLength;
}
} //Verify Signature
private static int VerifySignature(string sToken, string sTimeStamp, string sNonce, string sMsgEncrypt, string sSigture)
{ string hash = ""; int ret = 0;
ret = GenarateSinature(sToken, sTimeStamp, sNonce, sMsgEncrypt, ref hash); if (ret != 0) return ret; //System.Console.WriteLine(hash);
if (hash == sSigture) return 0; else
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_ValidateSignature_Error;
}
} public static int GenarateSinature(string sToken, string sTimeStamp, string sNonce, string sMsgEncrypt, ref string sMsgSignature)
{
ArrayList AL = new ArrayList();
AL.Add(sToken);
AL.Add(sTimeStamp);
AL.Add(sNonce);
AL.Add(sMsgEncrypt);
AL.Sort(new DictionarySort()); string raw = ""; for (int i = 0; i < AL.Count; ++i)
{
raw += AL[i];
}
SHA1 sha;
ASCIIEncoding enc; string hash = ""; try
{
sha = new SHA1CryptoServiceProvider();
enc = new ASCIIEncoding(); byte[] dataToHash = enc.GetBytes(raw); byte[] dataHashed = sha.ComputeHash(dataToHash);
hash = BitConverter.ToString(dataHashed).Replace("-", "");
hash = hash.ToLower();
} catch (Exception)
{ return (int)WXBizMsgCryptErrorCode.WXBizMsgCrypt_ComputeSignature_Error;
}
sMsgSignature = hash; return 0;
}
}
}在处理程序中,首先获取到公众平台服务器发送过来的数据,并转成字符串。代码如下
string postStr = "";
Stream s = VqiRequest.GetInputStream();//此方法是对System.Web.HttpContext.Current.Request.InputStream的封装,可直接代码
byte[] b = new byte[s.Length];
s.Read(b, 0, (int)s.Length);
postStr = Encoding.UTF8.GetString(b);然后再分别获取url中的参数:timestamp,nonce,msg_signature,encrypt_type。可以看到,在明文模式下是没有encrypt_type参数的。如图:
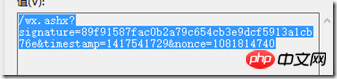
明文模式
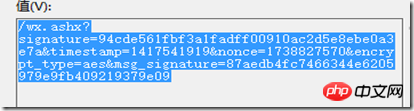
兼容模式和安全模式
兼容模式和安全模式则加入了消息体的签名与加密类型两个参数。
由于在实际的运营中,兼容模式不太可能使用,所以在此不做详细介绍了。
接着上面的讲。获取到url中的参数后,判断encrypt_type的值是否为aes,如果是则说明是使用的兼容模式或安全模式,此时则需调用解密相关的方法进行解密。
if (encrypt_type == "aes")
{
requestXML.IsAes = true;
requestXML.EncodingAESKey = aeskey;
requestXML.token = token;
requestXML.appid = appid; var ret = new MsgCrypt(token, aeskey, appid); int r = ret.DecryptMsg(msg_signature, timestamp, nonce, postStr, ref data); if (r!=0)
{
WxApi.Base.WriteBug("消息解密失败"); return null;
}
}否则则直接解析接收到的xml字符串。
下图是接收到的密文:
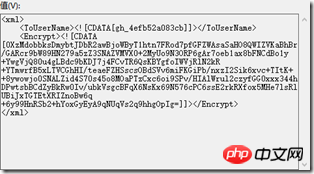
解密之后的内容如下:
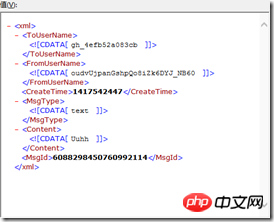
此时就可以解析此xml了。
当需要回复加密的请求时,回复的内容也是需要加密的,所以在回复前需要判断此条接收到的消息是否加密,如果是加密的,则需要将需要回复的内容加密后,再进行回复。回复消息的方法将在下一篇中具体讲解,此篇只讲解加密的过程。
处理代码如下:
private static void Response(WeiXinRequest requestXML, string data)
{ if (requestXML.IsAes)
{ var wxcpt = new MsgCrypt(requestXML.token, requestXML.EncodingAESKey, requestXML.appid);
wxcpt.EncryptMsg(data, Utils.ConvertDateTimeInt(DateTime.Now).ToString(), Utils.GetRamCode(), ref data);
}
Utils.ResponseWrite(data);
}将接收到的消息实体和需要回复的内容xml传递过来,如果是加密的,则加密后再Response,否则直接Response。
【相关推荐】
Atas ialah kandungan terperinci 微信开发之消息体签名和加解密. Untuk maklumat lanjut, sila ikut artikel berkaitan lain di laman web China PHP!

Alat AI Hot

Undresser.AI Undress
Apl berkuasa AI untuk mencipta foto bogel yang realistik

AI Clothes Remover
Alat AI dalam talian untuk mengeluarkan pakaian daripada foto.

Undress AI Tool
Gambar buka pakaian secara percuma

Clothoff.io
Penyingkiran pakaian AI

AI Hentai Generator
Menjana ai hentai secara percuma.

Artikel Panas

Alat panas

Notepad++7.3.1
Editor kod yang mudah digunakan dan percuma

SublimeText3 versi Cina
Versi Cina, sangat mudah digunakan

Hantar Studio 13.0.1
Persekitaran pembangunan bersepadu PHP yang berkuasa

Dreamweaver CS6
Alat pembangunan web visual

SublimeText3 versi Mac
Perisian penyuntingan kod peringkat Tuhan (SublimeText3)

Topik panas
 1377
1377
 52
52
 Bagaimana untuk mengesahkan tandatangan dalam PDF
Feb 18, 2024 pm 05:33 PM
Bagaimana untuk mengesahkan tandatangan dalam PDF
Feb 18, 2024 pm 05:33 PM
Kami biasanya menerima fail PDF daripada kerajaan atau agensi lain, sesetengahnya dengan tandatangan digital. Selepas mengesahkan tandatangan, kami melihat mesej SignatureValid dan tanda semak hijau. Sekiranya tandatangan tidak disahkan, kesahihannya tidak diketahui. Mengesahkan tandatangan adalah penting, mari lihat cara melakukannya dalam PDF. Cara Mengesahkan Tandatangan dalam PDF Mengesahkan tandatangan dalam format PDF menjadikannya lebih boleh dipercayai dan dokumen lebih cenderung untuk diterima. Anda boleh mengesahkan tandatangan dalam dokumen PDF dengan cara berikut. Buka PDF dalam Adobe Reader Klik kanan tandatangan dan pilih Show Signature Properties Klik butang Tunjukkan Sijil Penandatangan Tambah tandatangan pada senarai Sijil Dipercayai daripada tab Amanah Klik Sahkan Tandatangan untuk melengkapkan pengesahan Biarkan
 Tandatangan Outlook hilang setiap hari selepas dimulakan semula
Feb 19, 2024 pm 05:24 PM
Tandatangan Outlook hilang setiap hari selepas dimulakan semula
Feb 19, 2024 pm 05:24 PM
Tandatangan e-mel adalah penting untuk menunjukkan kesahihan dan profesionalisme dan termasuk maklumat hubungan dan logo syarikat. Pengguna Outlook sering mengadu bahawa tandatangan hilang selepas dimulakan semula, yang boleh mengecewakan bagi mereka yang ingin meningkatkan keterlihatan syarikat mereka. Dalam artikel ini, kami akan meneroka pelbagai pembetulan untuk menyelesaikan isu ini. Mengapakah tandatangan Microsoft Outlook saya terus hilang? Jika anda menggunakan Microsoft Outlook buat kali pertama, pastikan versi anda bukan versi percubaan. Versi percubaan boleh menyebabkan tandatangan hilang. Selain itu, seni bina versi juga harus sepadan dengan seni bina versi sistem pengendalian. Jika anda mendapati bahawa tandatangan e-mel anda hilang dari semasa ke semasa dalam Outlook Web App, ia mungkin disebabkan oleh
 Gunakan Python untuk melaksanakan penyulitan dan penyahsulitan RSA
Apr 14, 2023 pm 02:13 PM
Gunakan Python untuk melaksanakan penyulitan dan penyahsulitan RSA
Apr 14, 2023 pm 02:13 PM
Semalam saya melihat artikel Bahasa Inggeris [1] yang menunjukkan cara menggunakan Python untuk melaksanakan algoritma RSA Logik kod adalah sama seperti artikel sebelumnya Memahami Algoritma RSA boleh membaca artikel Memahami Algoritma RSA, yang menghadapi Apa itu RSA, prinsip matematik RSA diterangkan, dan contoh mudah boleh dikatakan bahawa ini adalah artikel paling mudah untuk memahami RSA di Quanzhihu (ini datang dari komen pembaca). Saya menjalankan kod yang disediakan dalam bahasa Inggeris dan mendapati ia tidak boleh menyulitkan bahasa Cina, jadi saya mengubah suai fungsi penyulitan dan penyahsulitan untuk menyokong penyulitan dan penyahsulitan bahasa Cina. Artikel hari ini akan berkongsi cara menggunakan Python untuk melaksanakan penyulitan RSA dan proses penyahsulitan untuk membantu anda mewujudkan
 Ciri baharu dalam PHP 8: Ditambah pengesahan dan tandatangan
Mar 27, 2024 am 08:21 AM
Ciri baharu dalam PHP 8: Ditambah pengesahan dan tandatangan
Mar 27, 2024 am 08:21 AM
PHP8 ialah versi PHP terkini, membawa lebih banyak kemudahan dan fungsi kepada pengaturcara. Versi ini mempunyai tumpuan khusus pada keselamatan dan prestasi, dan salah satu ciri baharu yang perlu diberi perhatian ialah penambahan keupayaan pengesahan dan tandatangan. Dalam artikel ini, kita akan melihat dengan lebih dekat ciri baharu ini dan kegunaannya. Pengesahan dan tandatangan adalah konsep keselamatan yang sangat penting dalam sains komputer. Ia sering digunakan untuk memastikan bahawa data yang dihantar adalah lengkap dan sahih. Pengesahan dan tandatangan menjadi lebih penting apabila berurusan dengan transaksi dalam talian dan maklumat sensitif kerana jika seseorang dapat mengganggu data, ia berpotensi
 Menandatangani dan pengesahan dalam PHP
May 23, 2023 pm 04:10 PM
Menandatangani dan pengesahan dalam PHP
May 23, 2023 pm 04:10 PM
Dengan perkembangan teknologi Internet, keselamatan telah menjadi isu yang semakin penting, terutamanya keselamatan data yang dihantar dalam aplikasi Internet. Teknologi pengesahan tandatangan dan tandatangan telah menjadi cara penting untuk memastikan keselamatan data PHP, sebagai bahasa pengaturcaraan Internet yang popular, juga menyediakan fungsi berkaitan untuk pengesahan tandatangan dan tandatangan Artikel ini akan memperkenalkan pengesahan tandatangan dan tandatangan. 1. Konsep tandatangan dan pengesahan tandatangan Tandatangan merujuk kepada penyulitan data untuk menghasilkan rentetan tertentu berdasarkan algoritma tandatangan digital. Data boleh disahkan melalui rentetan ini
 Kaedah pengesahan tandatangan dan aplikasinya dalam PHP
Aug 06, 2023 pm 07:05 PM
Kaedah pengesahan tandatangan dan aplikasinya dalam PHP
Aug 06, 2023 pm 07:05 PM
Kaedah dan Aplikasi Pengesahan Tandatangan dalam PHP Dengan perkembangan Internet, keselamatan aplikasi Web menjadi semakin penting. Pengesahan tandatangan ialah mekanisme keselamatan biasa yang digunakan untuk mengesahkan kesahihan permintaan dan menghalang akses tanpa kebenaran. Artikel ini akan memperkenalkan kaedah pengesahan tandatangan dan aplikasinya dalam PHP, dan memberikan contoh kod. 1. Apakah pengesahan tandatangan? Pengesahan tandatangan ialah mekanisme pengesahan berdasarkan kunci dan algoritma Parameter permintaan disulitkan untuk menghasilkan nilai tandatangan yang unik Pelayan kemudiannya menyahsulit permintaan dan mengesahkan tandatangan menggunakan algoritma dan kunci yang sama.
 Pembangunan PHP WeChat: Bagaimana untuk melaksanakan penyulitan dan penyahsulitan mesej
May 13, 2023 am 11:40 AM
Pembangunan PHP WeChat: Bagaimana untuk melaksanakan penyulitan dan penyahsulitan mesej
May 13, 2023 am 11:40 AM
PHP ialah bahasa skrip sumber terbuka yang digunakan secara meluas dalam pembangunan web dan pengaturcaraan sisi pelayan, terutamanya dalam pembangunan WeChat. Hari ini, semakin banyak syarikat dan pembangun mula menggunakan PHP untuk pembangunan WeChat kerana ia telah menjadi bahasa pembangunan yang benar-benar mudah dipelajari dan mudah digunakan. Dalam pembangunan WeChat, penyulitan dan penyahsulitan mesej merupakan isu yang sangat penting kerana ia melibatkan keselamatan data. Untuk mesej tanpa kaedah penyulitan dan penyahsulitan, penggodam boleh mendapatkan data dengan mudah, menimbulkan ancaman kepada pengguna.
 Menggunakan PHP untuk membangunkan alat pemesejan massa WeChat
May 13, 2023 pm 05:00 PM
Menggunakan PHP untuk membangunkan alat pemesejan massa WeChat
May 13, 2023 pm 05:00 PM
Dengan populariti WeChat, semakin banyak syarikat mula menggunakannya sebagai alat pemasaran. Fungsi pemesejan kumpulan WeChat ialah salah satu cara penting bagi perusahaan untuk menjalankan pemasaran WeChat. Walau bagaimanapun, jika anda hanya bergantung pada penghantaran manual, ia adalah tugas yang sangat memakan masa dan susah payah untuk pemasar. Oleh itu, adalah amat penting untuk membangunkan alat pemesejan massa WeChat. Artikel ini akan memperkenalkan cara menggunakan PHP untuk membangunkan alat penghantaran massa WeChat. 1. Kerja penyediaan Untuk membangunkan alat pemesejan massa WeChat, kita perlu menguasai perkara teknikal berikut: Pengetahuan asas PHP WeChat alat pembangunan platform awam: Sub




