12 key points often asked in redis interviews (with answers)
This article brings you a summary of some questions that are often asked during interviews Redis. It simulates how the interviewer goes into depth on the topic of Redis step by step, and comprehensively examines the candidate's understanding of Redis. I hope it will be helpful to everyone.

Recommended study: "2022 latest redis interview questions and answers"
Frequently asked questions in redis interviews 12 key points
Redis is an unavoidable threshold in interviews. As long as you write that you have used Redis in your resume, you will definitely not be able to escape.
Xiao Zhang:
Hello, interviewer. I'm here for an interview.
Interviewer:
Hello, Xiao Zhang. I have read your resume and I am proficient in Redis, so I will just ask you a few Redis-related questions. First of all, my question is, is Redis single-threaded or multi-threaded?
Xiao Zhang:
The threading model used in different versions of Redis is different. Before Redis version 4.0, the single-threaded model was used, and after version 4.0, it was increased Multi-threading support.
Before 4.0, although we said that Redis was single-threaded, it only meant that its network I/O thread and Set and Get operations were completed by one thread. However, Redis persistence and cluster synchronization are still completed using other threads.
After 4.0, multi-threading support was added, mainly reflected in the asynchronous deletion function of big data, such as unlink key, flushdb async, flushall async Wait
Interviewer:
The answer is very good, Then why did Redis choose to use single thread before 4.0? And is it so fast using single thread?
Xiao Zhang:
I think the main reason for choosing single thread is that it is simple to use, there is no lock competition, all operations can be completed without locks, and there are no deadlocks and threads Switching brings performance and time overhead, but at the same time, single thread cannot fully exert the performance of multi-core CPU.
As for why single thread is so fast, I think there are mainly the following reasons:
Most operations of Redis are completed in memory, and the execution efficiency in memory itself It is fast and uses efficient data structures such as hash tables and skip tables.
Using a single thread avoids multi-thread competition, saves the time and performance overhead caused by multi-thread switching, and does not cause deadlock.
The I/O multiplexing mechanism is used to handle a large number of client Socket requests, because it is based on a non-blocking I/O model, which allows Redis to efficiently communicate over the network. , the I/O read and write process is no longer blocked.
Interviewer:
Yes, How does Redis achieve no data loss?
Xiao Zhang:
Redis data is stored in the memory. In order to ensure that the Redis data is not lost, it is necessary to store the data from the memory to the disk so that it can be restarted after the server is restarted. Afterwards, the original data can be restored from the disk. This is the data persistence of Redis. There are three ways to persist Redis data.
AOF log (Append Only File, file append mode): records all operation commands and appends them to the file in the form of text.
RDB Snapshot (Redis DataBase): Write the memory data at a certain moment to the disk in binary form.
Hybrid persistence method: Redis 4.0 adds a new hybrid persistence method, integrating the advantages of RDB and AOF.
Interviewer:
Then please talk about the implementation principles of AOF and RDB respectively.
Xiao Zhang:
AOF uses post-write logging. Redis first executes the command to write the data into the memory, and then records the log to the file. The AOF log records operation commands, not actual data. If the AOF method is used for fault recovery, the entire log needs to be executed.
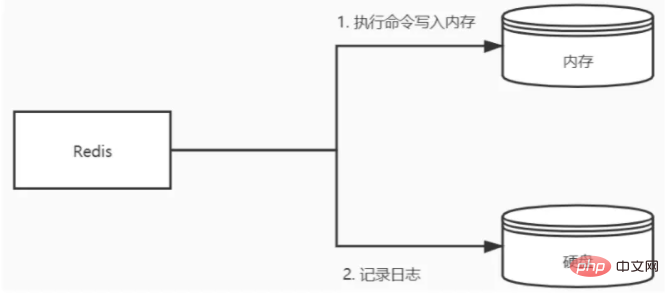
RDB uses a memory snapshot method. It records the data at a certain moment, not the operation. Therefore, when using the RDB method for fault recovery, you only need to directly The RDB file can be read into memory to achieve quick recovery.
Interviewer:
You just mentioned that AOF uses the "post-write log" method, while the MySQL we usually use uses the "pre-write log" method, then Why does Redis need to execute the command first and then write the data to the log?
Xiao Zhang: My forehead started to sweat. What are the questions you asked? . .
Well, this is mainly because Redis does not check the syntax of the command before writing it to the log, so it only records the successfully executed command to avoid recording the wrong command, and it is not possible to write the log after the command is executed. Will block the current write operation.
Interviewer:
What are the risks of writing a diary after ?
Xiao Zhang:
I... I don't know how to do this.
Interviewer:
Well, there are two main risks that may occur when writing logs:
Data may be lost: If Redis just After executing the command, if a failure occurs, the command may be lost.
May block other operations: AOF log is actually executed in the main thread, so when Redis writes the log file to disk, it will still block subsequent operations and cannot be executed.
I still have a question: Will RDB block threads when taking snapshots?
Xiao Zhang:
Redis provides two commands to generate RDB snapshot files, namely save and bgsave. The save command is executed in the main thread and will cause blocking. The bgsave command will create a child process for writing RDB files, avoiding blocking the main thread. This is also the default configuration of Redis RDB.
Interviewer:
RDB Can the data be modified when taking a snapshot?
Xiao Zhang:
Save is synchronous and will block client commands. It can be modified during bgsave.
Interviewer:
SoHow does Redis solve the problem of allowing data modification when bgsave takes a snapshot?
Xiao Zhang: (Why are you still asking...I™ don’t know how!)
Um, I’m not sure about this...
Interview Official:
This is mainly implemented using the sub-threads of bgsave. The specific operations are as follows:
If the main thread performs a read operation, the main thread and bgsave The sub-processes do not affect each other;
If the main thread performs a write operation, a copy of the modified data will be copied, and then bgsaveThe sub-process will write the copy data RDB file, during this process, the main thread can still directly modify the original data.
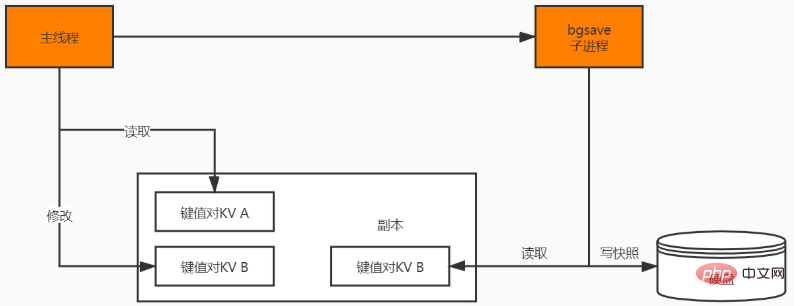
It should be noted that the frequency of Redis execution of RDB is very important, because this will affect the integrity of snapshot data and the stability of Redis, so after Redis 4.0, an additional AOF and RDB mixed data persistence mechanism: Write the data to the file in the form of RDB, and then store the subsequent operation commands in the file in the AOF format, which not only ensures the restart speed of Redis, but also reduces the data Risk of loss.
Xiao Zhang:
I learned it.
Interviewer:
Then can you tell me how Redis achieves high availability?
Xiao Zhang:
There are three main ways to achieve high availability in Redis: master-slave replication, sentinel mode, and Redis cluster.
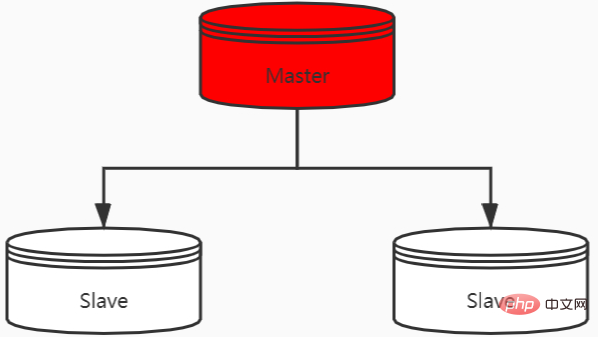
Master-slave replication
Synchronize data from a previous Redis server to multiple slave Redis servers, that is, a master-slave model. This is similar to MySQL The principle of master-slave replication is the same.
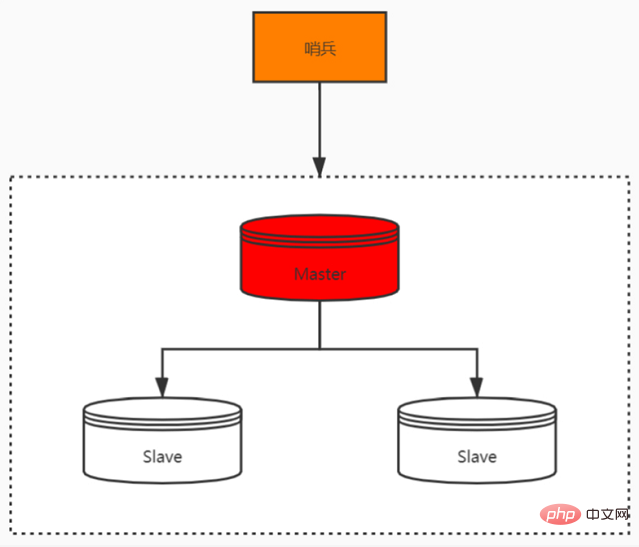
Sentinel Mode
When using the Redis master-slave service, there will be a problem, that is, when the Redis master-slave server appears When a failure occurs, manual recovery is required. In order to solve this problem, Redis added the sentinel mode (because the sentinel mode can monitor the master and slave servers and provide automatic disaster recovery functions).
Redis Cluster (Cluster)
Redis Cluster is a distributed and decentralized operating mode, which is based on Redis 3.0 The Redis cluster solution launched in the version distributes data on different servers to reduce the system's dependence on a single master node, thereby improving the read and write performance of the Redis service.
Interviewer:
Use the sentinel mode to ensure that there is a copy of the data, and there is a sentinel monitoring on the availability. Once the master goes down, the slave will be elected. The node is the master node, which already meets the needs of our production environment. So why do we still need to use cluster mode?
Xiao Zhang:
Well, the sentinel mode is still the master-slave mode. In the master-slave mode, we can expand the read concurrency capability by adding salve nodes, but there is no way to expand it. Writing capacity and storage capacity, storage capacity can only be the upper limit that the master node can carry. Therefore, in order to expand writing capabilities and storage capabilities, we need to introduce cluster mode.
Interviewer:
There are so many Master nodes in the cluster, how does the redis cluster determine which node to choose when storing?
Xiao Zhang:
This should be using some kind of hash algorithm, but I’m not sure. . .
Interviewer:
Okay, that’s it for today’s interview. You go back and wait for our interview notification.
Xiao Zhang:
Okay, thank you interviewer, can you tell me how redis cluster implements node selection?
Interviewer:
Redis Cluster uses a consistent hash algorithm to implement node selection. As for what a consistent hash algorithm is, you can go back and see for yourself .
Redis Cluster divides itself into 16384 Slots. Hash slots are similar to data partitions. Each key-value pair will be mapped to a hash slot according to its key. Specific execution The process is divided into two major steps.
Calculate a 16-bit value based on the key of the key-value pair according to the CRC16 algorithm.
Then use the 16bit value to modulo 16384 to get a modulus in the range of 0~16383. Each modulus represents a hash slot with a corresponding number.
Each Redis node is responsible for processing a part of the slots. If you have three master nodes ABC, the slots each node is responsible for are as follows:
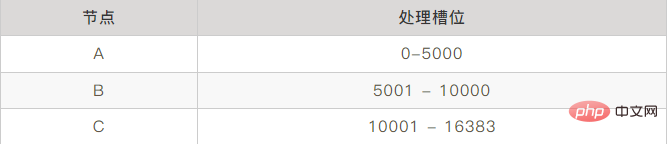
This implements the selection of cluster nodes.
Recommended learning: "Redis video tutorial", "2022 latest redis interview questions and answers"
The above is the detailed content of 12 key points often asked in redis interviews (with answers). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
How to build the redis cluster mode
Apr 10, 2025 pm 10:15 PM
Redis cluster mode deploys Redis instances to multiple servers through sharding, improving scalability and availability. The construction steps are as follows: Create odd Redis instances with different ports; Create 3 sentinel instances, monitor Redis instances and failover; configure sentinel configuration files, add monitoring Redis instance information and failover settings; configure Redis instance configuration files, enable cluster mode and specify the cluster information file path; create nodes.conf file, containing information of each Redis instance; start the cluster, execute the create command to create a cluster and specify the number of replicas; log in to the cluster to execute the CLUSTER INFO command to verify the cluster status; make
 How to implement the underlying redis
Apr 10, 2025 pm 07:21 PM
How to implement the underlying redis
Apr 10, 2025 pm 07:21 PM
Redis uses hash tables to store data and supports data structures such as strings, lists, hash tables, collections and ordered collections. Redis persists data through snapshots (RDB) and append write-only (AOF) mechanisms. Redis uses master-slave replication to improve data availability. Redis uses a single-threaded event loop to handle connections and commands to ensure data atomicity and consistency. Redis sets the expiration time for the key and uses the lazy delete mechanism to delete the expiration key.
 What to do if redis-server can't be found
Apr 10, 2025 pm 06:54 PM
What to do if redis-server can't be found
Apr 10, 2025 pm 06:54 PM
Steps to solve the problem that redis-server cannot find: Check the installation to make sure Redis is installed correctly; set the environment variables REDIS_HOST and REDIS_PORT; start the Redis server redis-server; check whether the server is running redis-cli ping.
 How to view all keys in redis
Apr 10, 2025 pm 07:15 PM
How to view all keys in redis
Apr 10, 2025 pm 07:15 PM
To view all keys in Redis, there are three ways: use the KEYS command to return all keys that match the specified pattern; use the SCAN command to iterate over the keys and return a set of keys; use the INFO command to get the total number of keys.
 How to read the source code of redis
Apr 10, 2025 pm 08:27 PM
How to read the source code of redis
Apr 10, 2025 pm 08:27 PM
The best way to understand Redis source code is to go step by step: get familiar with the basics of Redis. Select a specific module or function as the starting point. Start with the entry point of the module or function and view the code line by line. View the code through the function call chain. Be familiar with the underlying data structures used by Redis. Identify the algorithm used by Redis.
 How to use the redis command
Apr 10, 2025 pm 08:45 PM
How to use the redis command
Apr 10, 2025 pm 08:45 PM
Using the Redis directive requires the following steps: Open the Redis client. Enter the command (verb key value). Provides the required parameters (varies from instruction to instruction). Press Enter to execute the command. Redis returns a response indicating the result of the operation (usually OK or -ERR).
 How to read redis queue
Apr 10, 2025 pm 10:12 PM
How to read redis queue
Apr 10, 2025 pm 10:12 PM
To read a queue from Redis, you need to get the queue name, read the elements using the LPOP command, and process the empty queue. The specific steps are as follows: Get the queue name: name it with the prefix of "queue:" such as "queue:my-queue". Use the LPOP command: Eject the element from the head of the queue and return its value, such as LPOP queue:my-queue. Processing empty queues: If the queue is empty, LPOP returns nil, and you can check whether the queue exists before reading the element.
 How to use redis lock
Apr 10, 2025 pm 08:39 PM
How to use redis lock
Apr 10, 2025 pm 08:39 PM
Using Redis to lock operations requires obtaining the lock through the SETNX command, and then using the EXPIRE command to set the expiration time. The specific steps are: (1) Use the SETNX command to try to set a key-value pair; (2) Use the EXPIRE command to set the expiration time for the lock; (3) Use the DEL command to delete the lock when the lock is no longer needed.




