 Article Tags
Article Tags
-
All
-
web3.0
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Backend Development
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Web Front-end
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Database
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Operation and Maintenance
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Development Tools
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
PHP Framework
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Common Problem
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Other
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Tech
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
CMS Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Java
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
System Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Computer Tutorials
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Hardware Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Mobile Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Software Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
-
Mobile Game Tutorial
-

 Mac OS
Mac OS
-

 Linux Operation and Maintenance
Linux Operation and Maintenance
-

 Apache
Apache
-

 Nginx
Nginx
-

 CentOS
CentOS
-

 Docker
Docker
-

 LVS
LVS
-

 vagrant
vagrant
-

 debian
debian
-

 zabbix
zabbix
-

 kubernetes
kubernetes
-

 ssh
ssh
-

 fabric
fabric
-
What does select mean in I/O multiplexing?
select is used to monitor changes in the status of multiple file descriptors. That is, it is used to monitor whether the file descriptor read/write/exception status is ready. Function prototype: intselect(intnfds, fd_set*readfds, fd_set*writefds, fd_set*exceptfds, structtimeval*timeout); Several major disadvantages of select: (1) Every time select is called, the fd collection needs to be copied from user mode to kernel mode , this overhead will be very large when there are many fds (2) At the same time, each call to select requires the kernel to traverse all the passed in fds, this overhead will also be very large when there are many fds (3) s
May 13, 2023 pm 05:31 PM
How Javascript fills an array with data
Filling an Array with Data If we need to fill an array with some data, or need a data with the same value, we can use the fill() method. varplants=newArray(8).fill('8');console.log(plants);//['8','8','8','8','8','8',&#
May 13, 2023 pm 05:10 PM
What are the optimization techniques in website construction?
Many SEOers know the truth that "content is king and external links are king", but how do they understand "content"? Some SEOers think that content refers to the original articles on the site. This is understandable because it is indeed a basis for website construction. In fact, the content has a wider scope. The following will focus on this "content" to carry out on-site optimization. tricks. First: Why should URL be placed at the front in URL path design? This is because URL path design is very important. Users need to go through the path to access the website, so a reasonable URL design is not only convenient for users to view, but also conducive to search engine inclusion and improves search engine friendliness. If the URL design of the website is unreasonable, it will naturally affect the search index.
May 13, 2023 pm 04:58 PM
How to update firewall IP and access control during computer room changes
1. Introduction: 1. Connection method: External network-->Firewall-->Switch 2. Server migration, switching of all IP addresses 2. Change of IP configured in the firewall: For example: the old address is: 0.0.8.34; the new address is :0.0.0.82PS: The firewall can use multiple addresses to access the Internet. The premise is that the access network cable provides the function of allowing both old and new IP addresses to access the Internet. Therefore, you can first ensure that the new address is in normal use before deleting the old configuration. 1. Change the access address: a) Add a new access address: i. Use a network cable to connect to the corresponding network port (the usual network cable is enough, and older firewalls may need to use a crossover cable). This is the first time. network port (eth0). If your firewall is still the factory default access location
May 13, 2023 pm 04:16 PM
What is JIS-CTF_VulnUpload target drone strategy?
Vulnhub is one of my favorite playgrounds, and every target drone on it is a cool game. Completely finding all flags is only the basic task, and achieving privilege escalation is the ultimate goal. I am not pursuing the fastest capture of the flag, but rather using a complete attack chain to invade the target drone as much as possible. Therefore, some content in this guide may not be directly helpful for capturing the flag, but you should consider it when dealing with real targets. The target drone "JIS-CTF:VulnUpload" contains 5 flags and is of primary difficulty. It takes an average of 1.5 hours to complete the attack. You can get it from https://www.vulnhub.com/entry/jis-ctf-vulnupload,228/
May 13, 2023 pm 03:46 PM
Sample analysis of Sqlmap automated injection
Use sqlmap to automate injection into dvwa, set the dvwa level to low, open dvwa's SQLInjection (SQLInjection(Blind)), open browser debugging, enter the userid and submit, and view the intercepted requests. You can see that it is a GET request, the url "http://192.168.1.222:8089/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" We put it directly into salmap to test it, use the -u command -u"http ://192.168.1.22
May 13, 2023 pm 03:31 PM
How to use win10 remote desktop connection command
1. Enable local remote desktop. Through remote desktop connection, users can easily control computers in the company or other places at home. In this way, when users want to use certain functions of the company computer, they can do so at home. Of course, the company computer cannot be turned off. You also need to enable the remote connection function. If the user wants to connect to a remote computer, the computer needs to turn on the remote connection function and set the remote connection user. The setting method is as follows. 1. Open the Control Panel and click the "System" command in the pop-up window. 2. Click the "Remote Settings" text link. In the "System" window that opens, click the "Remote Settings" text link on the left side of the window. 3. Click the "Select User" button. In the pop-up "System Properties" dialog box, select "Remote"
May 13, 2023 pm 02:31 PM
How to implement array deduplication in Javascript
Array deduplication 1. from() superimposed newSet() method. To deduplicate strings or numerical arrays, you can directly use the from method. varplants=['Saturn','Earth','Uranus','Mercury','Venus','Earth','Mars','Jupiter&am
May 13, 2023 pm 02:07 PM
How to conduct AppleJeus action analysis
The Lazarus organization is one of the most active APT organizations currently. In 2018, Kaspersky discovered an attack campaign called AppleJeus launched by this organization. This operation is Lazarus's first attack on macOS users. In order to attack macOS users, Lazarus developed macOS malware and added an authentication mechanism. It can download the payload of the latter stage very carefully and without dropping the disk. Load the next stage payload. To attack Windows users, they developed a multi-stage infection process. After the "AppleJeus" operation analysis was released, Lazarus became more cautious when conducting attacks and adopted more methods to avoid being attacked.
May 13, 2023 pm 01:58 PM
How to analyze APK security and automate auditing
1. Small talk When it comes to mobile security, you may be unfamiliar with it, because research in this area has only gradually become popular in recent years. So what is mobile security? First of all, we know that mobile security is nothing more than some security issues on the iOS platform and Android platform, including some issues in the platform system itself and issues at the application level. Of course, some communication protocols need to be involved when the client and server interact, mainly http and https protocols, and of course some other protocols, such as websocket and so on. We won’t pay too much attention to the flaws of these protocols themselves. What we need to pay attention to is whether the data packets are encrypted when necessary during transmission, and whether the server has the right to operate the user.
May 13, 2023 pm 12:07 PM
How to solve the ZipperDown vulnerability
Attack conditions for the ZipperDown security vulnerability: 1. The App uses ZipArchive2, a zip package delivered by the App is not encrypted during transmission, and the zip package is not encrypted. 3. The App uses JSPatch or other execution engines, and the local script is not encrypted. The script can be executed as long as it is placed in the specified directory, and the legality of the local script is not verified. 4. Users connect to unreliable WIFI hotspots for network communication. Methods to circumvent this vulnerability; developers' own circumvention methods: 1. Repair the SSZipArchive library , in the unzipFileAtPath decompression function, intercept the "../" string that may cause directory traversal. 2. Communication between client and server
May 13, 2023 am 11:55 AM
How to understand vCenter Server and host management
vCenterServer and host management - vCenterServer connection When using vSphereClient to connect to vCenterServer, you can manage vCenterServer and all the hosts and virtual machines it manages. 1. Run VMwarevSphereClient locally and log in as an administrator; enter the IP address or vCenterServer name; enter the Windows administrator user name ; Enter the Windows administrator password 2. When connecting to vCenter Server for the first time after installation, there is no object in the list. 2. Host management creates a data center: equivalent to a container, hosts in the same data center can do
May 13, 2023 am 11:49 AM
What are the javascript functions used by Baidu Maps?
JS functions used in Baidu Map developed by javascript //Create and initialize map functions: functioninitMap(){createMap();//Create a map setMapEvent();//Set map events addMapControl();//Add controls to the map addMarker();//Add marker to the map}//Create map function: functioncreateMap(){varmap=newBMap.Map("container");//Create a map in the Baidu map container varpoint=newB
May 13, 2023 am 11:40 AM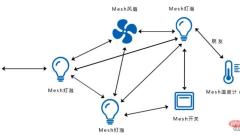
What are the differences between mesh networking and wireless bridging?
1. Networking mode 1. Wireless bridging is point-to-point or point-to-multipoint networking communication, which is mainly based on directional transmission. 2. Mesh means that all devices have equal status in the wireless network, and any network node can access the wired network. 2. Distance 1. Wireless bridging is mainly based on fixed point monitoring, and different antenna selections are selected according to different scenarios. 2. The characteristic of mesh is that it is very flexible in deployment. The antennas used with Mesh ad hoc network equipment are mainly omnidirectional antennas, which can quickly establish the system. 3. Transmission rate 1. The design transmission rate of the bridge is mainly 300Mbps and 866Mbps. Specifications 2. The configuration of the antenna is mainly omnidirectional antenna, which has relatively large attenuation. Therefore, the speed is not obvious compared with traditional bridges. Four, pass
May 13, 2023 am 11:37 AM
Hot tools Tags

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

vc9-vc14 (32+64 bit) runtime library collection (link below)
Download the collection of runtime libraries required for phpStudy installation

VC9 32-bit
VC9 32-bit phpstudy integrated installation environment runtime library

PHP programmer toolbox full version
Programmer Toolbox v1.0 PHP Integrated Environment

VC11 32-bit
VC11 32-bit phpstudy integrated installation environment runtime library

SublimeText3 Chinese version
Chinese version, very easy to use

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1318
1318
 25
25
 1269
1269
 29
29
 1248
1248
 24
24




