current location:Home > 安全通�%A search
Found a total of 21321 related content
-

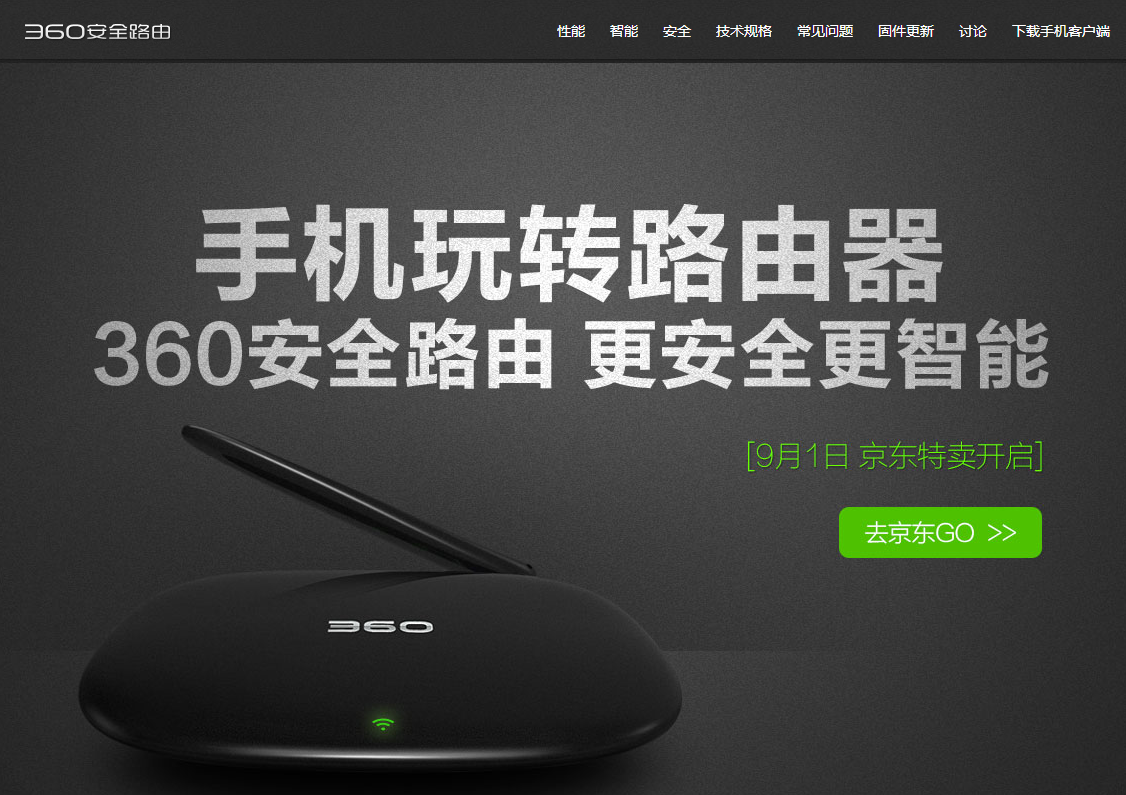
- 360 security router full screen scrolling effect
- 360 security router full screen scrolling effect
- 2019-10-18 161 1461
-

- Cheetah Safe Browser special page full-screen scrolling up and down switching special effects JS code
- The special page of Cheetah Safe Browser has full-screen scrolling and up and down switching special effect JS code. The scrolling effect is very smooth. It is implemented based on jQuery. The effect is captured from the Cheetah website. It is a very good special guide page.
- 2017-01-13 178 2271
-

- jQuery+CSS3 elastic transition full-screen page turning effect
- A page that can be switched in full screen by clicking the navigation button
- 2023-02-09 148 1030
-

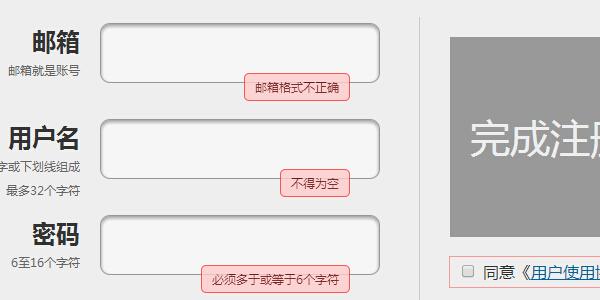
- Registration verification instance member registration form verification code
- Registration verification example member registration form verification code is used to verify whether the user's registered member information meets the requirements. If not, re-enter it. It also increases security. PHP Chinese website recommends downloading!
- 2017-02-07 251 2453
-

- Pokemon elf ball background animation special effects
- Create full-screen Poke Ball falling background animation and cartoon Pokemon game background animation special effects based on canvas.
- 2021-03-05 230 2541
-

- Official website of Blue Security Protection Company
- Official website of Blue Security Protection Company
- 2018-01-02 224 3027151
-

- Blue security protection company website template
- Blue security protection company website template
- 2018-01-18 178 2959888
-

- Financial security encryption technology responsive web template
- Financial security encryption technology responsive web template
- 2018-01-25 136 2928165
-

- Giant Bicycle official website full set of website template download
- Download the full set of website templates for Giant Bicycle's official website.
- 2017-01-18 176 3582815
-

- Digital Systems Security Services Company Website Template
- Digital system security services company website template is a promotional website template download suitable for companies engaged in data and information security services. Tip: This template calls the Google font library, and the page may open slowly.
- 2023-11-13 135 973
-

- PHP Security Basics (Chinese version)
- PHP Security Basics (Chinese version)
- 2018-02-10 332 2868043
-

- Network Security Basics Tutorial
- Network Security Basics Tutorial
- 2018-01-22 222 2943598
-

- Proficient in JavaScript+jQuery: Completely Master the Code of Dynamic Web Design
- Proficient in JavaScript+jQuery: Completely Master the Code of Dynamic Web Design
- 2018-01-05 269 3012375
-

- Han Shunping's complete set of notes from entry to proficiency in PHP
- Han Shunping, graduated from Tsinghua University, is a well-known senior lecturer in software training in China. He has worked at Sina, Click Technology, and UFIDA. Host or participate in "Sina Mail System", "Orange SNS (Social Network) Website", "Click Technology Collaboration Software Group Server (Linux/Solaris Platform)", "National General Staff Voice Monitoring System", "English Learning Machine System" ", "UFIDA ERP (U8 Product) System" and other projects. Rich practical experience, patient and meticulous teaching, easy to understand, courageous to practice, diligent in innovation, teaching style close to life, teaching language vivid and interesting, many years
- 2017-12-12 600 3098576
-

- PHP+MySQL commercial website construction practice
- Chapter 1 Getting Started with Linux 1-1 Characteristics of operating systems 1-2 Installation settings 1-2-1 hard disk partition 1-2-2 Set LILO 1-2-3 Network address and time zone settings l-2-4 Set the account passwords of system administrators and general users 1-2-5 system safety certification l-2-6 Select the installation kit 1-2-7 Set up the display card and test Xwindows l-2-8 Start installing the kit l-3 Common commands l-4 basic network settings
- 2017-12-11 349 3103632
-

- HD pictures of cute cartoon characters and family portraits
- Cute Cartoon Characters Family Portrait HD Picture Free Download JPG HD Picture Cartoon Cartoon Character Family Portrait
- 2017-04-06 130 3772
-

- Hard hat, wrench, hammer and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as a hard hat, a wrench, a hammer, a vise and a screwdriver. It is available in AI and EPS formats, including JPG preview.
- 2023-09-19 108 781
-

- Hard hat, hammer, wrench and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as a hard hat, hammer, wrench, screwdriver and triangle ruler. It is available in AI and EPS formats, including JPG preview.
- 2023-09-12 102 876
-

- Hard hat wrench vise and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as hard hats, wrenches, vise, screwdrivers, screws and nuts. It is available in AI and EPS formats, including JPG preview.
- 2023-09-19 112 799
-

- Round texture metal frame mobile phone android system application button icon material
- Round metal icon, mobile phone button icon material, Android system icon, cartoon character expression icon, phone help icon
- 2017-03-13 172 1572
-

- Android security and permissions WORD version
- This document mainly talks about the security and permissions of Android; Android is a multi-process system, and each application (and system component) runs in its own process. I hope this document will help friends in need; interested friends can come and take a look.
- 2024-01-28 2 2117
-

- Development of Bluetooth communication system based on Android word version
- With the popularity of android mobile phones, the demand for android applications is growing. This huge potential market has attracted countless software development manufacturers and developers to join it. The openness of Android makes it more attractive to young people than Apple and Blackberry, and can attract the attention and love of young people. Among those aged 18 to 24, Android is the most popular operating system. At the same time, because the openness of the Android system has laid the foundation for the rapid development of Android tablets, it has also attracted more and more users to accept and use it.
- 2024-02-28 46 905
-

- ANDROID Bluetooth programming WORD document doc format
- Using the BluetoothAdapter class, you can find surrounding Bluetooth devices on your Android device and then pair (bind) them. Bluetooth communication is transmitted to each other based on the unique address MAC. Considering security issues, Bluetooth communication needs to be paired first. Then start to connect to each other. After the connection, the devices will share the same RFCOMM channel to transmit data to each other. Currently, these implementations are implemented on Android 2.0 or higher SDK. 1. Finding/discovering dev
- 2024-02-27 48 1249
-

- Hive permission control Chinese WORD version
- Hive can control permissions through metadata from version 0.10 (including version 0.10) onwards. In versions before Hive-0.10, permissions are mainly controlled through Linux users and user groups. CREATE, SELECT, and DROP of Hive tables cannot be controlled. Of course, Hive's control of permissions based on metadata is not completely safe. The purpose is to prevent users from accidentally doing operations they shouldn't do. Interested friends can come and take a look
- 2024-02-03 31 1635
-

- 150 Examples of Delphi 7 Application Programming Full Book Content CHM Edition
- Download the CHM book with 150 Examples of Delphi 7 Application Programming. The book mainly uses 150 examples to comprehensively and in-depth introduce the common methods and techniques of developing applications with Delphi 7. It mainly explains the use of Delphi 7 for interface effect processing, image processing, Graphics and multimedia development, system function control, file processing, network and database development, and component application, etc. These examples are simple and practical, highly typical, and have outstanding functions. The technologies used in many examples can be slightly expanded to solve similar problems. The best way to use this book is to learn from examples
- 2024-01-18 2 991
-

- Server security dog
- Server security dog
- 2018-02-03 300 5159
-

- win2003 server security
- win2003 server security
- 2018-02-03 213 4846
-

- Website content security protection
- Website content security protection
- 2018-02-03 213 5070
-

- Server iis security expert
- Server iis security expert
- 2018-02-03 214 4919
-

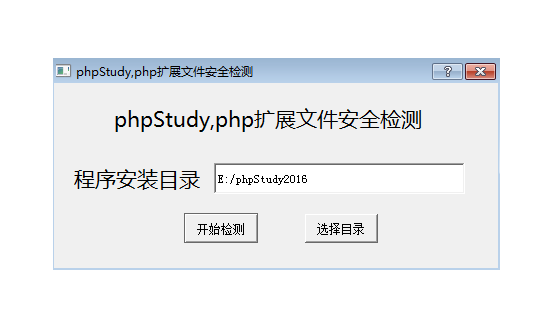
- phpstudy security self-check fix
- phpstudy2016/2018 security detection and repair
- 2019-09-23 862 22349
-

- phpseclib-masterPHP secure communication library
- phpseclib-masterPHP secure communication library
- 2017-12-08 149 1399
-

- SecurityMultiTool-masterPHP security library
- SecurityMultiTool-masterPHP security library
- 2017-12-19 292 4718
-

- PHP security, anti-injection class
- PHP security, anti-injection class
- 2017-12-26 227 2306
-

- SecurityMultiTool-master a PHP security library
- SecurityMultiTool-master a PHP security library
- 2017-12-08 144 1327
-

- PHP's safe string class
- PHP's safe string class
- 2017-03-31 242 5530