current location:Home > 資訊安全 search
Found a total of 21313 related content
-
- 360 security router full screen scrolling effect
- 360 security router full screen scrolling effect
- 2019-10-18 44 1153
-

- Cheetah Safe Browser special page full-screen scrolling up and down switching special effects JS code
- The special page of Cheetah Safe Browser has full-screen scrolling and up and down switching special effect JS code. The scrolling effect is very smooth. It is implemented based on jQuery. The effect is captured from the Cheetah website. It is a very good special guide page.
- 2017-01-13 75 1923
-
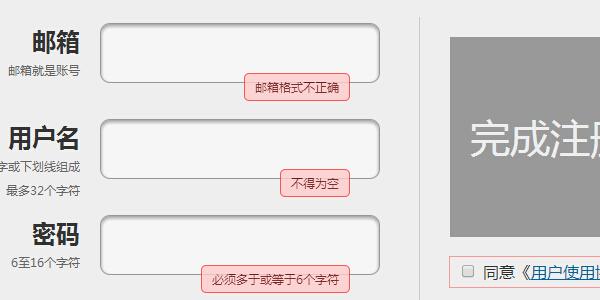
- Registration verification instance member registration form verification code
- Registration verification example member registration form verification code is used to verify whether the user's registered member information meets the requirements. If not, re-enter it. It also increases security. PHP Chinese website recommends downloading!
- 2017-02-07 152 2027
-

- Mobile Happy Scratch HTML5 plug-in
- The mobile Happy Scratch HTML5 plug-in is a mobile H5 Scratch plug-in suitable for Double 12 activities.
- 2024-02-29 5 343
-
- HTML5 paper folded into gift box animation special effects
- The HTML5 paper folding into gift box animation effect is a Christmas gift animation effect implemented in CSS that is suitable for Christmas or any holiday.
- 2024-02-29 5 327
-
- Official website of Blue Security Protection Company
- Official website of Blue Security Protection Company
- 2018-01-02 113 3026960
-
- Blue security protection company website template
- Blue security protection company website template
- 2018-01-18 76 2959732
-
- Financial security encryption technology responsive web template
- Financial security encryption technology responsive web template
- 2018-01-25 30 2927978
-
- Giant Bicycle official website full set of website template download
- Download the full set of website templates for Giant Bicycle's official website.
- 2017-01-18 73 3582609
-
- Digital Systems Security Services Company Website Template
- Digital system security services company website template is a promotional website template download suitable for companies engaged in data and information security services. Tip: This template calls the Google font library, and the page may open slowly.
- 2023-11-13 24 710
-
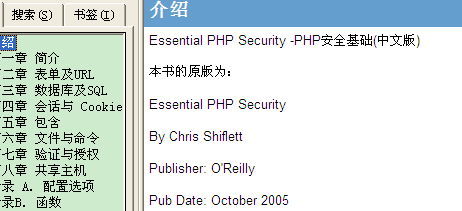
- PHP Security Basics (Chinese version)
- PHP Security Basics (Chinese version)
- 2018-02-10 332 2867875
-

- Network Security Basics Tutorial
- Network Security Basics Tutorial
- 2018-01-22 222 2943468
-

- PHP+MySQL commercial website construction practice
- Chapter 1 Getting Started with Linux 1-1 Characteristics of operating systems 1-2 Installation settings 1-2-1 hard disk partition 1-2-2 Set LILO 1-2-3 Network address and time zone settings l-2-4 Set the account passwords of system administrators and general users 1-2-5 system safety certification l-2-6 Select the installation kit 1-2-7 Set up the display card and test Xwindows l-2-8 Start installing the kit l-3 Common commands l-4 basic network settings
- 2017-12-11 349 3103499
-

- Self-study PHP, MySQL and Apache
- This book combines PHP development with MySQL applications, and provides an in-depth and simple analysis of PHP and MySQL respectively. It not only introduces the general concepts of PHP and MySQL, but also gives a more comprehensive explanation of the web applications of PHP and MySQL, and includes several Classic and practical example. This book is the 4th edition, which has been completely updated, rewritten and expanded, including the latest improved features of PHP5.3 (for example, better error and exception handling), MySQL's stored procedures and storage engine, Ajax technology and Web2 .0 and the security issues that web applications need to pay attention to
- 2017-12-09 303 3107704
-

- PHP network programming technology and examples (Cao Yanlong)
- Detailed explanation of PHP network programming technology from shallow to deep, comprehensively and systematically introduces PHP development technology, and provides a large number of examples for readers to practice in practice. In addition, the author has specially recorded corresponding supporting teaching videos for this book to help readers better learn the content of this book. These videos are included on the companion CD together with the example source code in the book. This book is divided into 4 parts. The first part is PHP preparation, which introduces the advantages, development environment and installation of PHP; the second part is PHP basics, which introduces constants and variables, operators and expressions, process control and functions in PHP; the third part is This is an advanced chapter, an introduction.
- 2017-12-08 271 3111495
-
- Hard hat, wrench, hammer and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as a hard hat, a wrench, a hammer, a vise and a screwdriver. It is available in AI and EPS formats, including JPG preview.
- 2023-09-19 1 413
-
- Hard hat, hammer, wrench and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as a hard hat, hammer, wrench, screwdriver and triangle ruler. It is available in AI and EPS formats, including JPG preview.
- 2023-09-12 0 562
-

- Hard hat wrench vise and other tools design Labor Day vector material (AI+EPS)
- This is a Labor Day vector material designed with tools such as hard hats, wrenches, vise, screwdrivers, screws and nuts. It is available in AI and EPS formats, including JPG preview.
- 2023-09-19 2 341
-

- Clown popping out of the box design April Fools' Day vector material (AI+EPS)
- This is an April Fool's Day vector material designed by a clown popping out of a box. It is available in AI and EPS formats, including JPG preview.
- 2023-08-31 0 378
-

- Red-nosed clown popping out of the box design April Fools' Day vector material (AI+EPS)
- This is an April Fool's Day vector material designed by a red-nosed clown popping out of a box. It is available in AI and EPS formats, including JPG preview.
- 2023-08-31 0 348
-

- Android security and permissions WORD version
- This document mainly talks about the security and permissions of Android; Android is a multi-process system, and each application (and system component) runs in its own process. I hope this document will help friends in need; interested friends can come and take a look.
- 2024-01-28 2 1925
-

- Hive permission control Chinese WORD version
- Hive can control permissions through metadata from version 0.10 (including version 0.10) onwards. In versions before Hive-0.10, permissions are mainly controlled through Linux users and user groups. CREATE, SELECT, and DROP of Hive tables cannot be controlled. Of course, Hive's control of permissions based on metadata is not completely safe. The purpose is to prevent users from accidentally doing operations they shouldn't do. Interested friends can come and take a look
- 2024-02-03 0 1432
-

- Android Development Guide Chinese PDF version
- Android development guide Chinese pdf version, friends who learn android can refer to it. Application Fundamentals Key Classes Application Components Activation Components: Intent Close Component Manifest File Intent Filter Activity and Task Affinity (Attraction) and New Task Loading Mode Clean Stack Start Task Process and Thread Process Thread Remote Procedure Call Thread Safe Method Component Life cycleActivi
- 2024-02-26 0 614
-

- ANDROID Bluetooth programming WORD document doc format
- Using the BluetoothAdapter class, you can find surrounding Bluetooth devices on your Android device and then pair (bind) them. Bluetooth communication is transmitted to each other based on the unique address MAC. Considering security issues, Bluetooth communication needs to be paired first. Then start to connect to each other. After the connection, the devices will share the same RFCOMM channel to transmit data to each other. Currently, these implementations are implemented on Android 2.0 or higher SDK. 1. Finding/discovering dev
- 2024-02-27 0 977
-

- RMI remote method call word version
- Raza Microelectronics, Inc. (RMI) is a leader in innovative semiconductor solutions for information infrastructure. Its products are widely used to improve the evolving information infrastructure. In this evolution process, the connections between data centers and homes are gradually upgraded in terms of strength and speed; security and intelligence have become requirements for every network system environment; at the same time, edge networks are increasingly becoming bottlenecks, prompting the industry to need more Intelligent network access method with scalability and cost advantages. RMI designs and provides a variety of information infrastructure
- 2024-01-27 0 933
-

- Server security dog
- Server security dog
- 2018-02-03 136 4762
-

- win2003 server security
- win2003 server security
- 2018-02-03 78 4512
-

- Website content security protection
- Website content security protection
- 2018-02-03 64 4728
-

- Server iis security expert
- Server iis security expert
- 2018-02-03 61 4533
-
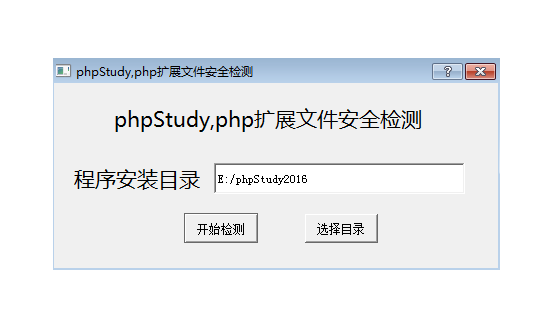
- phpstudy security self-check fix
- phpstudy2016/2018 security detection and repair
- 2019-09-23 743 21891
-
- SecurityMultiTool-masterPHP security library
- SecurityMultiTool-masterPHP security library
- 2017-12-19 173 4270
-
- PHP security, anti-injection class
- PHP security, anti-injection class
- 2017-12-26 125 2086
-
- phpseclib-masterPHP secure communication library
- phpseclib-masterPHP secure communication library
- 2017-12-08 43 1196
-
- SecurityMultiTool-master a PHP security library
- SecurityMultiTool-master a PHP security library
- 2017-12-08 60 1161
-
- PHP's safe string class
- PHP's safe string class
- 2017-03-31 133 5181

