current location:Home > python安装后不见了 search
Found a total of 21313 related content
-
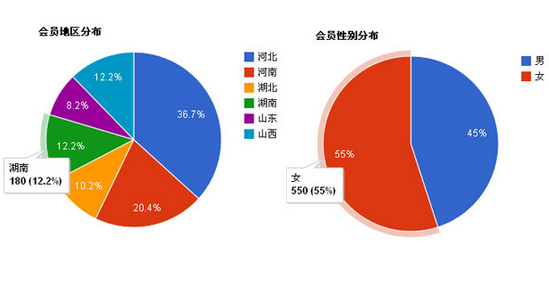
- Practical percentage jQuery pie chart plugin
- It's a pretty good jQuery pie chart plug-in. It's very convenient to load data and output it directly in the table, and then draw a pie chart to show the percentage. When you put the mouse over it, the data with the desired proportion will be displayed. It's still very good, although it doesn't. Highcharts.js is so powerful, at least it is enough for pie charts.
- 2017-01-14 142 2888
-

- Mobile Happy Scratch HTML5 plug-in
- The mobile Happy Scratch HTML5 plug-in is a mobile H5 Scratch plug-in suitable for Double 12 activities.
- 2024-02-29 5 343
-
- HTML5 paper folded into gift box animation special effects
- The HTML5 paper folding into gift box animation effect is a Christmas gift animation effect implemented in CSS that is suitable for Christmas or any holiday.
- 2024-02-29 5 327
-

- Pure CSS3 retro film player special effects
- Pure CSS3 retro film player special effects is a simple film music player and film recording player special effects.
- 2024-02-29 6 478
-
- HTML5 video player window floating code
- The HTML5 video player window floating code is a black and beautiful MP4 video player code.
- 2024-02-29 6 571
-
- Atmospheric Black IT Blog Mobile Adaptive Empire CMS Template
- The atmospheric black IT blog mobile adaptive Empire CMS template, the program released this time has integrated the Empire CMS data. Start the installation after deleting e/install/install.off, and restore the database after installation.
- 2017-01-19 131 3582136
-

- The entire source code of the education and training institution website
- Unzip the compressed package, upload it to the FTP space, and install it according to the normal installation steps of DreamWeaver; After the installation is completed, restore the database, specify the template folder in the system settings, and then update the cache to generate the home page, content page and list page for use. When calling the home page, the call ID needs to be modified in some places.
- 2017-02-20 178 3574289
-
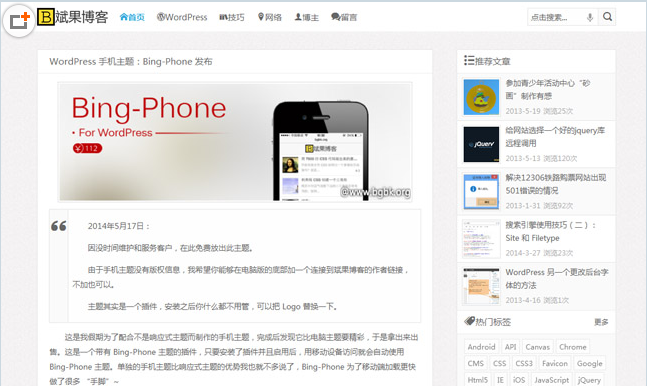
- WP Mobile Bing-Phone Theme
- The WP mobile device Bing-Phone theme is a mobile theme. The theme has a Bing-Phone theme plug-in. As long as the plug-in is installed and enabled, the Bing-Phone theme will be automatically used when accessed from a mobile device.
- 2017-06-09 282 3508069
-
- dede imitation of the most popular site template source code
- Contains plug-ins, one-click deletion of products, automatic collection of Taobao products, publishing articles for SEO, and many others. I won’t introduce them one by one. Dede is an imitation. The program structure is clear. You can get started in 1 minute. It is very powerful! Collect products by yourself, automatically collect articles, and set a random number of likes! Third-party login template, you can log in to Weibo, QQ, and Taobao! Installation method, install DEDE, restore the database after logging in.
- 2017-02-20 152 3572520
-
- Imitation Baidu Space Zblog 2.0 template download
- This theme is the zblog2.0 version theme. When installing, please log in to the zblog2.0 backend management, select the local jiyi.zba file in the theme management, submit it and activate it for use. The theme comes with the shortcut key Ctrl+enter for submission and does not support IE6. The theme comes with a sidebar plug-in, which can be configured and used in the background plug-in management.
- 2017-01-21 157 3581763
-
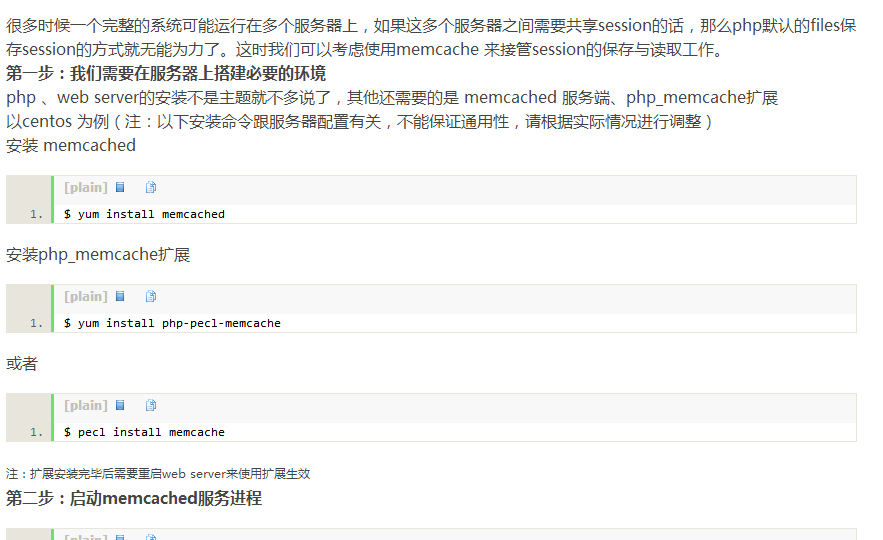
- PHP realizes memcache sharing of multi-server session sharing
- This article is a continuation of PHP's NFS sharing of multi-server session sharing, but this time, I use memcache to store sessions. Please see here for the installation of memcache: Build an efficient, reliable, and stable WEB server
- 2017-12-08 341 3111279
-

- Comprehensive practical (Vue3+Laravel8+Uniapp) courseware
- Comprehensive practical (Vue3+Laravel8+Uniapp) courseware
- 2023-06-26 34 1340
-

- ThinkPHP6 backend management payment system--practical development courseware
- ThinkPHP6 backend management payment system--practical development courseware
- 2024-05-09 36 1329
-

- PHP+MySQL basic introductory course courseware
- PHP+MySQL basic introductory course courseware
- 2023-11-06 32 1049
-

- HTML5CSS3JavaScriptES6 introductory course courseware
- HTML5CSS3JavaScriptES6 introductory course courseware
- 2023-11-06 56 914
-

- Clown popping out of the box design April Fools' Day vector material (AI+EPS)
- This is an April Fool's Day vector material designed by a clown popping out of a box. It is available in AI and EPS formats, including JPG preview.
- 2023-08-31 0 378
-

- Red-nosed clown popping out of the box design April Fools' Day vector material (AI+EPS)
- This is an April Fool's Day vector material designed by a red-nosed clown popping out of a box. It is available in AI and EPS formats, including JPG preview.
- 2023-08-31 0 348
-

- Colorful beautiful floral design spring background vector material (AI+EPS)
- This is a spring background vector material designed with colorful and beautiful flowers. It is available in AI and EPS formats, including JPG preview.
- 2023-08-31 1 368
-
- 14 different types of dinosaur vector materials (EPS+PNG)
- This is a different kind of dinosaur vector material, available in EPS and PNG formats, including JPG preview.
- 2023-08-31 1 508
-
- Tyrannosaurus rex with open mouth side vector material (EPS+PNG)
- This is a side vector material of a Tyrannosaurus rex with its mouth open. It is available in EPS and PNG formats, including a JPG preview.
- 2023-08-31 0 386
-

- Ruby User Guide Chinese HD Version CHM Format
- First, you have to check whether Ruby is installed. At the shell prompt (here represented as "%", so don't type %), type % ruby -v (-v tells the interpreter to print out the Ruby version) , and then press Enter. If Ruby is installed, you will see information similar to the following: % ruby -v ruby 1.6.6 [i586-linux] If Ruby is not installed, you can ask the administrator to install it, or you can do it yourself, Ruby is a language with no installation or usage restrictions
- 2024-01-30 0 1071
-

- Using Eclipse to build Maven's SpringMVC project Chinese WORD version
- First, Eclipse needs to install the Maven plug-in. Use MyEclipse to install the Maven plug-in. There are some problems with the built Maven project. First, when publishing tomcat, resources are never published to tomcat; second, after changing the classes under WEB-INF to the classes under target, I don’t know why MyEclipse still generates classes under WEB-INF. Either it really doesn’t generate classes in WEB-INF but releases t
- 2024-02-28 0 674
-

- Hive permission control Chinese WORD version
- Hive can control permissions through metadata from version 0.10 (including version 0.10) onwards. In versions before Hive-0.10, permissions are mainly controlled through Linux users and user groups. CREATE, SELECT, and DROP of Hive tables cannot be controlled. Of course, Hive's control of permissions based on metadata is not completely safe. The purpose is to prevent users from accidentally doing operations they shouldn't do. Interested friends can come and take a look
- 2024-02-03 0 1432
-

- Easy Language Learning Manual Ten Days Illustrated Tutorial to Learn Easy Language pdf version
- The Ten Days to Learn Easy Language Illustrated Tutorial provides a vivid and systematic explanation of the usage and operating techniques of Easy Language in the form of illustrations. Friends who need it can download it and take a look! The whole book is divided into ten chapters and is completed in ten days. The first chapter introduces the installation of Yi Language and the interface after operation. At the same time, a very simple small program is introduced to help users get started. Finally, we introduce the input methods of programming and some common problems encountered by beginners. Chapter 2 will touch on some specific issues, such as how to write a program that equals 1+2, and understand the concept of variables, the valid range of variables, data types and other knowledge.
- 2024-02-28 0 816
-

- Python essential reference pdf version
- This book provides an essential reference on the beautiful language python. The author brings you into the paradise of python through a complete and clear introductory guide, and then discusses syntax, types and objects, operators and expressions, control flow functions and functional programming, class and object-oriented programming, modules and packages, input and output , execution environment and other aspects are given detailed explanations. If you want to join the world of python, don't miss this book by David M beazley. (The cover is from the latest English version, the Chinese version seems to have only been translated to the second edition)
- 2024-01-26 1 828
-
- WIKINDX
- Reference management, document management, citations and more. Designed by scholars for scholars, continuously developed since 2003 and used by individuals and major research institutions worldwide, WIKINDX is a virtual research environment (enhanced online literature manager) that stores searchable references, notes, documents, Quotes, thoughts, etc. The integrated WYSIWYG word processor exports formatted articles to RTF and HTML. Plug-ins include a citation style editor and import/export of references (BibTeX, Endnote, RIS, etc.). WIKINDX supports every reference text
- 2023-10-07 23 4395
-
- CiviCRM
- CiviCRM is an open source and free to download member relationship management solution for advocacy, non-profit and other organizations. For more information, visit http://civicrm.org
- 2023-10-07 24 4482
-
- Joomla
- Joomla! is an award-winning content management system (CMS) that allows users to build websites and powerful online applications. It's very easy to use, stable and secure, with thousands of free extensions and templates.
- 2023-09-25 20 3945
-
- phpList
- phpList provides open source email marketing services, including analysis, list segmentation, content personalization and bounce processing. The rich technical functions and secure and stable code base are the result of 17 years of continuous development. Used in 95 countries, available in more than 20 languages, and used in 25 billion email campaigns sent last year. You can deploy it with your own SMTP server or get a free hosting account at http://phplist.com.
- 2023-09-18 15 4111
-
- SecLists
- SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.
- 2023-09-11 30 5741
-
- A collection of 50 excellent classic PHP algorithms
- Classic PHP algorithm, learn excellent ideas and expand your thinking
- 2020-03-26 2147 24412
-
- PHPExcel-1.8 class library (worth collecting!)
- PHPExcel PHP class library for operating Office Excel documents
- 2018-09-26 11352 90802
-
- Encryption PHP library for generating unique strings from integers
- Encryption PHP library for generating unique strings from integers
- 2018-01-23 307 9388
-
- Annotation-based PHP encryption library
- Annotation-based PHP encryption library
- 2018-01-23 177 7749
-
- PHP library for processing text
- PHP library for processing text
- 2018-01-23 306 9825


