由于redis没有配置,黑客利用redis安全漏洞入侵了服务器。
服务器cpu占用率一直处于高位,用top命令发现有个进程
(/usr/sbin/tplink -B -a cryptonight -o stratum+tcp://xmr.crypto-pool.fr:3333 -u 43rBm98TWYnJdGhHmPChR7)
非常吃cpu,于是用kill命令杀,发现提示无相关进程号,说明进程号是伪造的,不是真实的。于是直接删除这个文件/usr/sbin/tplink,可以删除。但是重启服务器之后,这个进程又出来了,然后查看了开机启动等文件都没有发现异常。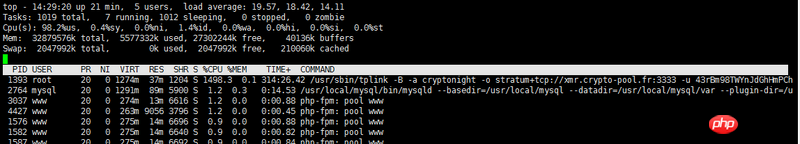
接着,通过rkhunter工具分析发现很多命令被篡改了。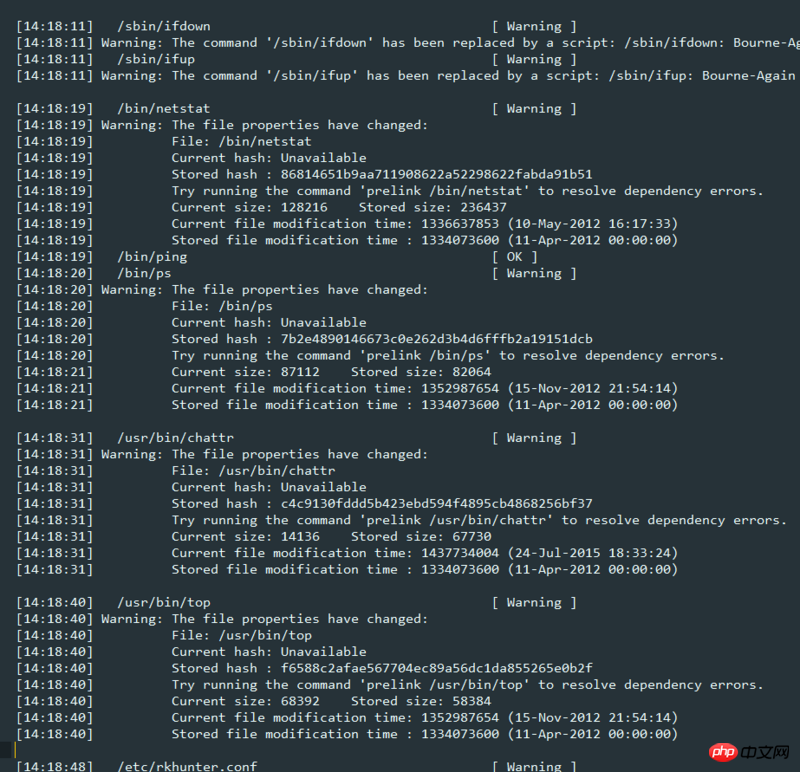
接着用另外一台正常的服务器程序替换所有被篡改的文件。
然后重启,所有相关文件又被篡改。
redis.conf也没办法正常配置,启动redis-server 如果后面带了redis.conf配置文件就没法启动,不带redis.conf就能够启动。卸载了redis,然后重新安装redis,依然无法解决。
跪求大神相助,这些问题如何解决,如何彻底清除该木马。
Look at this: link description
Also a reminder, it is best to set a password for redis, and it is best to use versions after 2.8. Versions 2.8 and earlier may have vulnerabilities
1. Modify the default port
2. Make auth stronger
3. Bind ip
4. Modify the configuration file and do not allow the execution of the config command
If you are infected, just do the system, it is simple and effective. This virus can be easily logged into the server, and anything can be injected into it. It is too troublesome to detoxify. . .
If the configuration is written correctly, the configuration file can be specified. If it must be exposed to the external network, you can add authentication in the configuration. It is also recommended to change the port. 6379 is too dangerous. .
The service cannot be exposed to the public network. Files will be written through redis-related operations, and your situation will occur. I have never encountered it, but I know it happens...