
This article mainly introduces the folder permission setting skills of the Win2008 R2 WEB serverSecurity Setting Guide, friends in need can refer to the following
Through the control file folder permissions to improve site security.
Permission settings in this article include two aspects, one is the permissions of the system directory and drive letter, and the other is the permission settings of the upload folder of the application.
System directory
Make sure that all drive letters are in NTFS format. If not, you can use the command convert d:/fs:ntfs to convert to NTFS format.
All disk root directories only give system and administrators permissions, othersdelete.
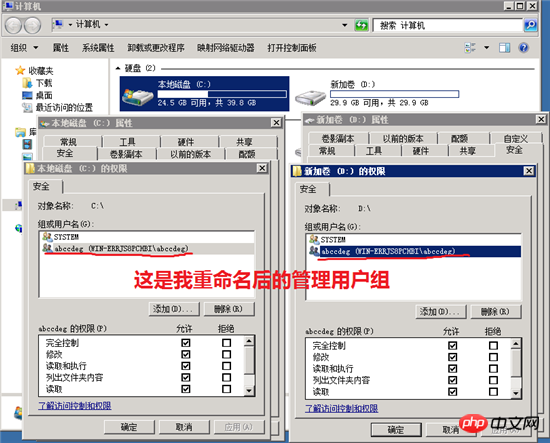
There will be several prompts for the system drive letter, just confirm it directly. Before doing this step, your operating environment software must be installed before you can do it. Otherwise, it may cause software installation errors. Remember that all security operation settings must be done after the software is installed.
Site directory
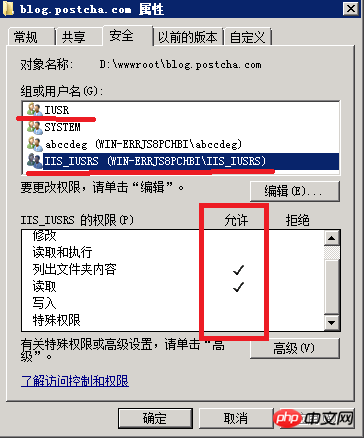
Each website corresponds to a directory, and add IUSR and IIS_IUSRS permissions to this website directory, which only give "list folder content" and "read" permissions.
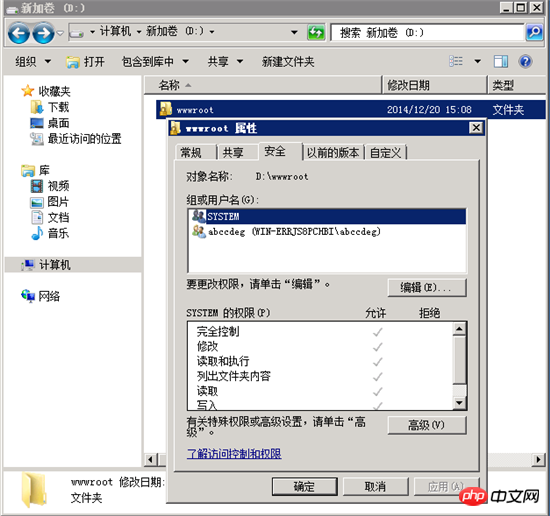
For example, I created a wwwroot directory in the root directory of drive D, and then created a blog.postcha.com directory in it. This directory contains my website program. Among them, wwwroot only needs to inherit the permissions of the d disk, and for the blog.postcha.com directory, we need to add two more permissions, namely IUSR and IIS_IUSRS.
wwwroot permissions:
Site directory permissions:
General All websites have the function of uploading files and pictures, but the files uploaded by users are not trustworthy. Therefore, the upload directory must be set separately. To upload the directory, you also need to add "modify" and "write" permissions to the IIS_IUSRS group.
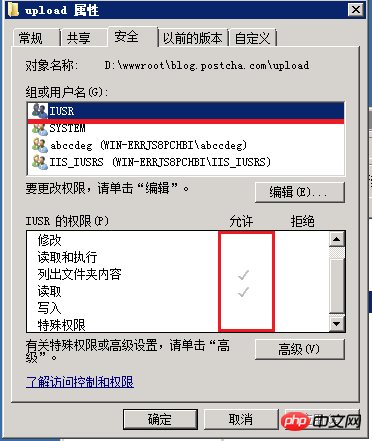
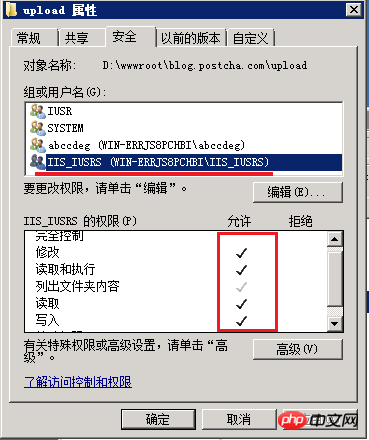
After the above setting, with an execution permission, once the user uploads a malicious file, our server It fell, but we have to give it here, so we have to cooperate with IIS to set it up again.
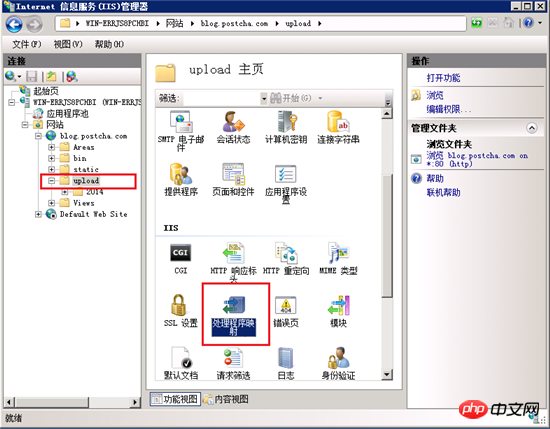
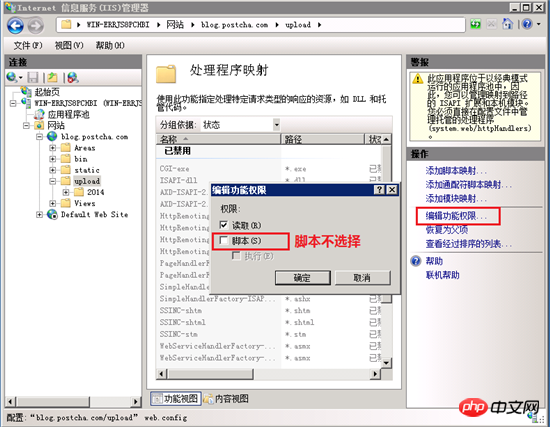
In iis7 and above, this setting is very convenient. Open the IIS manager, find the site, select the upload directory, double-click under IIS in the middle column to open "Handler Mapping", then select "Edit Function Permissions" and uncheck "Script".
Okay, let’s open the upload folder and see if there is an extra web.config.
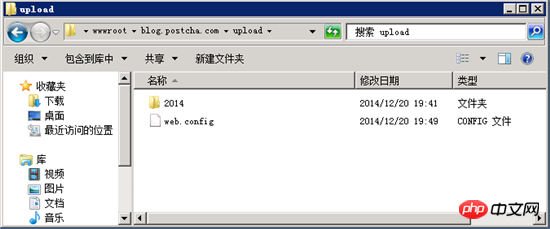
The content in web.config is as follows:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read" />
</system.webServer>
</configuration>means all files in the upload directory (including all subfolders) will only have read-only permissions. In this way, even if the user uploads a malicious file, it will not be effective.
Each website program has different functions and settings. Minimum permissions are maximum security.
The above is the detailed content of Win2008 R2 WEB Server Security Settings Guide - Folder Permission Setting Tips. For more information, please follow other related articles on the PHP Chinese website!
 How to turn off win10 upgrade prompt
How to turn off win10 upgrade prompt
 The difference between lightweight application servers and cloud servers
The difference between lightweight application servers and cloud servers
 CMD close port command
CMD close port command
 The difference between external screen and internal screen broken
The difference between external screen and internal screen broken
 How to jump with parameters in vue.js
How to jump with parameters in vue.js
 Cell sum
Cell sum
 How to intercept harassing calls
How to intercept harassing calls
 virtual digital currency
virtual digital currency




