GitHub 上有哪些安全相关的 Python 项目值得一读?
包括但不限于binary web
回复内容:
网络https://github.com/dloss/python-pentest-tools sqlmap github 上有人专门整理过列表(dloss/python-pentest-tools · GitHub),虽然并不是很完备,但总体上还是不错的一份单子。Scapy: send, sniff and dissect and forge network packets. Usable interactively or as a library
pypcap, Pcapy and pylibpcap: several different Python bindings for libpcap
libdnet: low-level networking routines, including interface lookup and Ethernet frame transmission
dpkt: fast, simple packet creation/parsing, with definitions for the basic TCP/IP protocols
Impacket: craft and decode network packets. Includes support for higher-level protocols such as NMB and SMB
pynids: libnids wrapper offering sniffing, IP defragmentation, TCP stream reassembly and port scan detection
Dirtbags py-pcap: read pcap files without libpcap
flowgrep: grep through packet payloads using regular expressions
Knock Subdomain Scan, enumerate subdomains on a target domain through a wordlist
Mallory, extensible TCP/UDP man-in-the-middle proxy, supports modifying non-standard protocols on the fly
Pytbull: flexible IDS/IPS testing framework (shipped with more than 300 tests)
调试和逆向工程Paimei: reverse engineering framework, includes PyDBG, PIDA, pGRAPH
Immunity Debugger: scriptable GUI and command line debugger
mona.py: PyCommand for Immunity Debugger that replaces and improves on pvefindaddr
IDAPython: IDA Pro plugin that integrates the Python programming language, allowing scripts to run in IDA Pro
PyEMU: fully scriptable IA-32 emulator, useful for malware analysis
pefile: read and work with Portable Executable (aka PE) files
pydasm: Python interface to the libdasm x86 disassembling library
PyDbgEng: Python wrapper for the Microsoft Windows Debugging Engine
uhooker: intercept calls to API calls inside DLLs, and also arbitrary addresses within the executable file in memory
diStorm: disassembler library for AMD64, licensed under the BSD license
python-ptrace: debugger using ptrace (Linux, BSD and Darwin system call to trace processes) written in Python
vdb / vtrace: vtrace is a cross-platform process debugging API implemented in python, and vdb is a debugger which uses it
Androguard: reverse engineering and analysis of Android application
FuzzingSulley: fuzzer development and fuzz testing framework consisting of multiple extensible components
Peach Fuzzing Platform: extensible fuzzing framework for generation and mutation based fuzzing (v2 was written in Python)
antiparser: fuzz testing and fault injection API
TAOF, (The Art of Fuzzing) including ProxyFuzz, a man-in-the-middle non-deterministic network fuzzer
untidy: general purpose XML fuzzer
Powerfuzzer: highly automated and fully customizable web fuzzer (HTTP protocol based application fuzzer)
SMUDGE
Mistress: probe file formats on the fly and protocols with malformed data, based on pre-defined patterns
Fuzzbox: multi-codec media fuzzer
Forensic Fuzzing Tools: generate fuzzed files, fuzzed file systems, and file systems containing fuzzed files in order to test the robustness of forensics tools and examination systems
Windows IPC Fuzzing Tools: tools used to fuzz applications that use Windows Interprocess Communication mechanisms
WSBang: perform automated security testing of SOAP based web services
Construct: library for parsing and building of data structures (binary or textual). Define your data structures in a declarative manner
fuzzer.py (feliam): simple fuzzer by Felipe Andres Manzano
Fusil: Python library used to write fuzzing programs
WebRequests: elegant and simple HTTP library, built for human beings
HTTPie: human-friendly cURL-like command line HTTP client
ProxMon: processes proxy logs and reports discovered issues
WSMap: find web service endpoints and discovery files
Twill: browse the Web from a command-line interface. Supports automated Web testing
Ghost.py: webkit web client written in Python
Windmill: web testing tool designed to let you painlessly automate and debug your web application
FunkLoad: functional and load web tester
spynner: Programmatic web browsing module for Python with Javascript/AJAX support
python-spidermonkey: bridge to the Mozilla SpiderMonkey JavaScript engine; allows for the evaluation and calling of Javascript scripts and functions
mitmproxy: SSL-capable, intercepting HTTP proxy. Console interface allows traffic flows to be inspected and edited on the fly
pathod / pathoc: pathological daemon/client for tormenting HTTP clients and servers
取证Volatility: extract digital artifacts from volatile memory (RAM) samples
LibForensics: library for developing digital forensics applications
TrIDLib, identify file types from their binary signatures. Now includes Python binding
aft: Android forensic toolkit
恶意程序分析pyew: command line hexadecimal editor and disassembler, mainly to analyze malware
Exefilter: filter file formats in e-mails, web pages or files. Detects many common file formats and can remove active content
pyClamAV: add virus detection capabilities to your Python software
jsunpack-n, generic JavaScript unpacker: emulates browser functionality to detect exploits that target browser and browser plug-in vulnerabilities
yara-python: identify and classify malware samples
phoneyc: pure Python honeyclient implementation
Didier Stevens' PDF tools: analyse, identify and create PDF files (includes PDFiD, pdf-parserand make-pdf and mPDF)
Opaf: Open PDF Analysis Framework. Converts PDF to an XML tree that can be analyzed and modified.
Origapy: Python wrapper for the Origami Ruby module which sanitizes PDF files
pyPDF: pure Python PDF toolkit: extract info, spilt, merge, crop, encrypt, decrypt…
PDFMiner: extract text from PDF files
python-poppler-qt4: Python binding for the Poppler PDF library, including Qt4 support
MiscInlineEgg: toolbox of classes for writing small assembly programs in Python
Exomind: framework for building decorated graphs and developing open-source intelligence modules and ideas, centered on social network services, search engines and instant messaging
RevHosts: enumerate virtual hosts for a given IP address
simplejson: JSON encoder/decoder, e.g. to use Google's AJAX API
PyMangle: command line tool and a python library used to create word lists for use with other penetration testing tools
Hachoir: view and edit a binary stream field by field
py-mangle: command line tool and a python library used to create word lists for use with other penetration testing tools
其他有用的py库和工具
BpythonIPython: enhanced interactive Python shell with many features for object introspection, system shell access, and its own special command system
Beautiful Soup: HTML parser optimized for screen-scraping
matplotlib: make 2D plots of arrays
Mayavi: 3D scientific data visualization and plotting
RTGraph3D: create dynamic graphs in 3D
Twisted: event-driven networking engine
Suds: lightweight SOAP client for consuming Web Services
M2Crypto: most complete OpenSSL wrapper
NetworkX: graph library (edges, nodes)
Pandas: library providing high-performance, easy-to-use data structures and data analysis tools
pyparsing: general parsing module
lxml: most feature-rich and easy-to-use library for working with XML and HTML in the Python language
Whoosh: fast, featureful full-text indexing and searching library implemented in pure Python
Pexpect: control and automate other programs, similar to Don Libes `Expect` system
Sikuli, visual technology to search and automate GUIs using screenshots. Scriptable inJython
PyQt and PySide: Python bindings for the Qt application framework and GUI library
另外需要额外提一点,大多数的 python 安全项目只适合看一看,没必要读一读,因为很多安全项目的工程架构、编码规范其实都一般般,了其概要便足够了。 是不是python没有考察,自己总结的一份关于信息安全的开源工具集。
WALA:对java字节码和javascript提供静态分析
PIXY:php静态分析工具,(污点分析)
clang:编译器的前端工作,负责词法分析和语法分析,生成语法树。
llvm:编译器的后端工作,负责中间码的生成,代码优化,机器码的生成。
klee: 适用于c语言,静态符号执行工具,建立在llvm之上。
magic:静态模型检测工具,适用于c语言
blast:静态模型检测工具,适用于c语言
java pathfinder: 静态模型检测工具,适用于java语言
Saturn(stanford): 基于定理证明的静态漏洞检测工具,适用于c语言
ESC/JAVA:基于定理证明的静态漏洞检测工具,适用于java
Peach:大名鼎鼎的fuzz框架。
Sulley(2012):新一代fuzz框架,python实现。
Argos:动态污点技术,用于主机蜜罐,检测0day攻击。
BitBlaze: 静态分析组件vine和动态分析组件temu都是开源。但是线上动态符号执行组件不开源。
valgrind:开源虚拟机,用于动态二进制分析。拥有内存分配分析和线程分析等等。动态二进制插桩的代表。只能实现用户态跟踪
TaintDroid: android动态污点分析工具
BAP:基于二进制可执行程序反汇编的漏洞模式检测工具。OCaml语言编写。
BinNavi:基于二进制可执行程序反汇编的漏洞模式检测工具。不能反汇编,需要借助IDA Pro对二进制文件反汇编。
Z3:微软开源的约束求解器。具有跨平台特性
STP:MIT开源协议的开源软件。在符号执行中广泛应用。但只能运行在Linux平台下。 逆向工程、二进制分析的工具:
qira BinaryAnalysisPlatform/qira · GitHub
angr angr/angr · GitHub the fuck greysign/thefuck · GitHub
没有理由不推荐它…… http://awesome-python.com/
这个网站上面列出的所有的库,都是一些优秀的第三方Python库,大部分托管在github上,都值得去认真阅读。 从题主问题出发,安全+值得读+python
requests不错,
创宇cos推荐sqlmap,
其他答案也有不错的工具。
好工具不一定值得读?!
本想推荐androguard 不过没读过!

熱AI工具

Undresser.AI Undress
人工智慧驅動的應用程序,用於創建逼真的裸體照片

AI Clothes Remover
用於從照片中去除衣服的線上人工智慧工具。

Undress AI Tool
免費脫衣圖片

Clothoff.io
AI脫衣器

Video Face Swap
使用我們完全免費的人工智慧換臉工具,輕鬆在任何影片中換臉!

熱門文章

熱工具

記事本++7.3.1
好用且免費的程式碼編輯器

SublimeText3漢化版
中文版,非常好用

禪工作室 13.0.1
強大的PHP整合開發環境

Dreamweaver CS6
視覺化網頁開發工具

SublimeText3 Mac版
神級程式碼編輯軟體(SublimeText3)
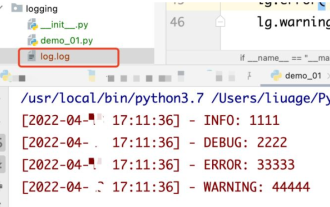 如何使用python+Flask實作日誌在web網頁即時更新顯示
May 17, 2023 am 11:07 AM
如何使用python+Flask實作日誌在web網頁即時更新顯示
May 17, 2023 am 11:07 AM
一、日誌輸出到檔案使用模組:logging可以產生自訂等級日誌,可以輸出日誌到指定路徑日誌等級:debug(偵錯日誌)=5){clearTimeout(time)//如果連續10次取得的都是空日誌清除定時任務}return}if(data.log_type==2){//如果取得到新日誌for(i=0;i
 Nginx的Web伺服器caddy怎麼使用
May 30, 2023 pm 12:19 PM
Nginx的Web伺服器caddy怎麼使用
May 30, 2023 pm 12:19 PM
Caddy簡介Caddy是一款功能強大,擴展性高的Web伺服器,目前在Github上已有38K+Star。 Caddy採用Go語言編寫,可用於靜態資源託管和反向代理。 Caddy具有以下主要特性:比較Nginx複雜的配置,其獨創的Caddyfile配置非常簡單;可以透過其提供的AdminAPI實現動態修改配置;預設支援自動化HTTPS配置,能自動申請HTTPS憑證並進行配置;能夠擴展到數以萬計的站點;可以在任意地方執行,沒有額外的依賴;採用Go語言編寫,內存安全更有保證。安裝首先我們直接在CentO
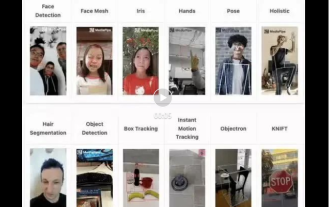 Web 端即時防擋臉彈幕(基於機器學習)
Jun 10, 2023 pm 01:03 PM
Web 端即時防擋臉彈幕(基於機器學習)
Jun 10, 2023 pm 01:03 PM
防擋臉彈幕,即大量彈幕飄過,但不會遮擋視訊畫面中的人物,看起來像是從人物背後飄過去的。機器學習已經火了好幾年了,但很多人都不知道瀏覽器中也能運行這些能力;本文介紹在視頻彈幕方面的實踐優化過程,文末列舉了一些本方案可適用的場景,期望能開啟一些腦洞。 mediapipeDemo(https://google.github.io/mediapipe/)展示主流防擋臉彈幕實現原理點播up上傳視訊伺服器後台計算提取視訊畫面中的人像區域,轉換成svg儲存用戶端播放視訊的同時,從伺服器下載svg與彈幕合成,人像
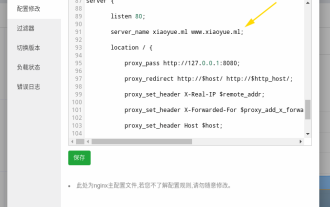 怎麼設定nginx保證frps伺服器與web共用80埠
Jun 03, 2023 am 08:19 AM
怎麼設定nginx保證frps伺服器與web共用80埠
Jun 03, 2023 am 08:19 AM
首先你會有個疑惑,frp是什麼呢?簡單的說frp就是內網穿透工具,配置客戶端以後,可以透過伺服器來存取內部網路。現在我的伺服器,已經用nginx做站了,80端口只有一個,那如果frp的服務端也想使用80端口,那該怎麼辦呢?經過查詢,這個是可以實現的,就是利用nginx的反向代理來實現。補充一下:frps就是伺服器端(server),frpc就是客戶端(client)。第一步:修改伺服器中nginx.conf設定檔在nginx.conf中http{}裡加入以下參數,server{listen80
 Java API 開發中使用 Jetty7 進行 Web 伺服器處理
Jun 18, 2023 am 10:42 AM
Java API 開發中使用 Jetty7 進行 Web 伺服器處理
Jun 18, 2023 am 10:42 AM
JavaAPI開發中使用Jetty7進行Web伺服器處理隨著互聯網的發展,Web伺服器已經成為了應用程式開發的核心部分,同時也是許多企業所關注的焦點。為了滿足日益增長的業務需求,許多開發人員選擇使用Jetty進行Web伺服器開發,其靈活性和可擴展性受到了廣泛的認可。本文將介紹如何在JavaAPI開發中使用Jetty7進行We
 如何使用Golang實作網頁應用程式的表單驗證
Jun 24, 2023 am 09:08 AM
如何使用Golang實作網頁應用程式的表單驗證
Jun 24, 2023 am 09:08 AM
表單驗證是Web應用程式開發中非常重要的環節,它能夠在提交表單資料之前對資料進行有效性檢查,避免應用程式出現安全漏洞和資料錯誤。使用Golang可以輕鬆實現網頁應用程式的表單驗證,本文將介紹如何使用Golang來實作網頁應用程式的表單驗證。一、表單驗證的基本要素在介紹如何實作表單驗證之前,我們需要知道表單驗證的基本要素是什麼。表單元素:表單元素是指
 web標準是什麼東西
Oct 18, 2023 pm 05:24 PM
web標準是什麼東西
Oct 18, 2023 pm 05:24 PM
Web標準是一組由W3C和其他相關組織制定的規範和指南,它包括HTML、CSS、JavaScript、DOM、Web可訪問性和性能優化等方面的標準化,透過遵循這些標準,可以提高頁面的兼容性、可訪問性、可維護性和效能。 Web標準的目標是使Web內容能夠在不同的平台、瀏覽器和裝置上一致地展示和交互,提供更好的使用者體驗和開發效率。
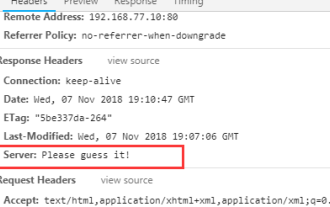 nginx隱藏版本號碼與WEB伺服器資訊問題怎麼解決
May 21, 2023 am 09:13 AM
nginx隱藏版本號碼與WEB伺服器資訊問題怎麼解決
May 21, 2023 am 09:13 AM
nginx不只可以隱藏版本信息,還支援自訂web伺服器資訊先看看最終的隱藏結果吧具體怎麼實現呢,其實也很簡單,請往下看1官網下載最新穩定版wgethttp://nginx.org/ download/nginx-1.14.1.tar.gz2解壓tar-xfnginx-1.14.1.tar.gzcdnginx-1.14.13修改c文件(1)vimsrc/http/ngx_http_header_filter_module.c #修改49行staticu_charngx_http_






