6月2日-每日安全知识热点
http://esevece.github.io/2016/06/01/taking-over-heroku-accounts.html
接管Heroku账号
https://www.nccgroup.trust/globalassets/our-research/us/whitepapers/2016/june/container_whitepaperpdf/
linux容器的权限和非权限的滥用
https://bogner.sh/2016/03/mitm-attack-against-keepass-2s-update-check/
通过中间人攻击,可以在keepass更新时,获取明文
http://blog.talosintel.com/2016/06/ropmemu.html
ROPMEMU:分析代码重用攻击的框架
https://grsecurity.net/SSTIC2016.pdf
SSTIC 2016 KEYNOTE
http://www.phdays.com/program/
phdays会议PPT开始提供下载
https://github.com/ANSSI-FR/polichombr
polichombr:恶意软件协同分析框架
https://github.com/wg/arc
用GO编写的安全文件打包程序
https://github.com/gentilkiwi/mimikatz/releases
mimikatz 20160602 (oe.eo) edition 发行
https://adaclscan.codeplex.com/
ADACLScan4.3.ps1 发行
https://olivierbeg.com/finding-xss-vulnerabilities-in-flash-files/
如果在flash文件中寻找xss漏洞
https://cyber-defense.sans.org/blog/2016/06/01/powershell-function-to-send-udp-syslog-message-packets
使用powershell发送udp syslog消息包
https://blogs.technet.microsoft.com/windowsserver/2016/05/26/securing-privileged-access-preventing-and-detecting-attacks/
为什么说权限访问重要:阻止和检测攻击
http://bitcoinist.net/sandjacking-ios-bitcoin-ethereum/
Sandjacking ios利用威胁比特币钱包
https://isc.sans.edu/diary/21123
针对DSHELL的网络取证第二部分
http://blog.securelayer7.net/mongodb-security-injection-attacks-with-php/
MongoDB安全,php中的注入攻击
http://www.slideshare.net/phdays/ss-62570233
WAF绕过
本文由 360安全播报 原创发布,如需转载请注明来源及本文地址。本文地址:http://bobao.360.cn/news/detail/3121.html

热AI工具

Undresser.AI Undress
人工智能驱动的应用程序,用于创建逼真的裸体照片

AI Clothes Remover
用于从照片中去除衣服的在线人工智能工具。

Undress AI Tool
免费脱衣服图片

Clothoff.io
AI脱衣机

AI Hentai Generator
免费生成ai无尽的。

热门文章

热工具

记事本++7.3.1
好用且免费的代码编辑器

SublimeText3汉化版
中文版,非常好用

禅工作室 13.0.1
功能强大的PHP集成开发环境

Dreamweaver CS6
视觉化网页开发工具

SublimeText3 Mac版
神级代码编辑软件(SublimeText3)

热门话题
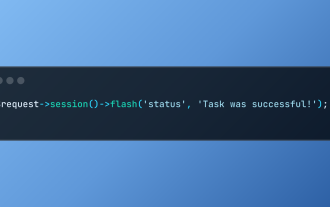 在Laravel中使用Flash会话数据
Mar 12, 2025 pm 05:08 PM
在Laravel中使用Flash会话数据
Mar 12, 2025 pm 05:08 PM
Laravel使用其直观的闪存方法简化了处理临时会话数据。这非常适合在您的应用程序中显示简短的消息,警报或通知。 默认情况下,数据仅针对后续请求: $请求 -
 php中的卷曲:如何在REST API中使用PHP卷曲扩展
Mar 14, 2025 am 11:42 AM
php中的卷曲:如何在REST API中使用PHP卷曲扩展
Mar 14, 2025 am 11:42 AM
PHP客户端URL(curl)扩展是开发人员的强大工具,可以与远程服务器和REST API无缝交互。通过利用Libcurl(备受尊敬的多协议文件传输库),PHP curl促进了有效的执行
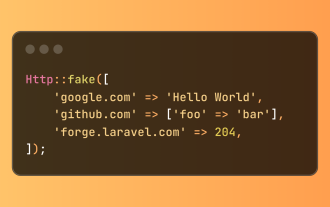 简化的HTTP响应在Laravel测试中模拟了
Mar 12, 2025 pm 05:09 PM
简化的HTTP响应在Laravel测试中模拟了
Mar 12, 2025 pm 05:09 PM
Laravel 提供简洁的 HTTP 响应模拟语法,简化了 HTTP 交互测试。这种方法显着减少了代码冗余,同时使您的测试模拟更直观。 基本实现提供了多种响应类型快捷方式: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 在Codecanyon上的12个最佳PHP聊天脚本
Mar 13, 2025 pm 12:08 PM
在Codecanyon上的12个最佳PHP聊天脚本
Mar 13, 2025 pm 12:08 PM
您是否想为客户最紧迫的问题提供实时的即时解决方案? 实时聊天使您可以与客户进行实时对话,并立即解决他们的问题。它允许您为您的自定义提供更快的服务
 解释PHP中晚期静态结合的概念。
Mar 21, 2025 pm 01:33 PM
解释PHP中晚期静态结合的概念。
Mar 21, 2025 pm 01:33 PM
文章讨论了PHP 5.3中引入的PHP中的晚期静态结合(LSB),从而允许静态方法的运行时分辨率调用以获得更灵活的继承。 LSB的实用应用和潜在的触摸









