Flex / PHP Security Basics
http://active6.com/blog/flex/flex-php-security-basics-part-one/
I've been creating Flash / PHP web sites and applications for years, but I am relatively new to Flex. After browsing the Adobe PHP samples for Flex earlier this week, I couldn't help but notice that some of this code could prove extremely hazardous if used in a public Flex site. This is no criticism, but since these examples will be read by virtually anyone who want to use the PHP / Flex tandem, it's probably not a bad idea to go over the security basics. I just love PHP. It's a great language for rapid development of dynamic site and application backends. Combined with the RIA power of Flex 2, there's no end to what you can do. But - as for every web programming language, security considerations for designing even the simplest web sites with Flex and PHP are crucial and often overlooked. This article makes some assumptions that on first look may linger on paranoia, but you should always remember the following when developing PHP / Flex apps:
It's dead easy to decompile a Flex or Flash file. The file format is public and many decompilers exist. It's equally easy to monitor requests and results from a Flex app to and from the server. This and the above make it a breeze to get the URI's and expected parameters for your PHP scripts. Most Flex/PHP tandem applications will expect and return clean, simple XML data. This data can be parsed easily to see if any security holes can be exploited.Many PHP features can lead to security holes. The PHP.net site as well as independent security initiatives (such as phpsec.org, the PHP Security Consortium) have identified a small dozen of "Top Security Blunders" that keep popping up. We'll go over these from a Flex perspective in this article. Understanding each possible flaw will help you avoid making the same mistakes in your PHP applications.
Unvalidated User InputThis may seem paranoid - but one of the most important rules of thumb for web development is that any data sent by a user should be considered as potentially malicious. Ignoring this leads to most of the exploits we'll review. Let's say we want construct a login panel. I've removed the unessential layout code:
[viewcode] src="flexsecurity/flexapp.xml" link="no" showsyntax="no" geshi="actionscript"[/viewcode]
As you can see, the Flex app will send a userid and password to a PHP script for login verification. All seems pretty standard doesn't it? Well - meet SQL Injection.
SQL InjectionSQL injection is essentially unvalidated user input. It allows exploitation of a database query. For example, you would check our Flex app's a userid/password set received against a user table. In MySQL, this would look something like:
SELECT * FROM users WHERE userid='$userid' AND password='$password';
A malicious user could enter "admin" as the userid and the following as his password:
' OR '1'='1
This results in the following query:
SELECT * FROM users WHERE userid='admin' AND pass='' OR '1'='1';
This bypasses validating the password - the user has gained entry as the administrator!
We need to neutralize malicious entries from the submitted values. In many PHP installations, this is already taken care of by the magic_quotes_gpc setting in the php.ini file. You can check this by using the phpinfo() function. In case magic quotes is set to Off, you must use PHP's addslashes() function:
$userid = addslashes($_REQUEST['userid']); $password = addslashes($_REQUEST['password']);
However, there is one unfortunate side-effect to this setting being enabled: every value passed back to your PHP scripts will have slashes added. I won't go into a discussion on what is the best setting here, because it really depends on the system you're building. (You can check the PHP documentation for details).
As a rule of thumb, always check the status of magic_quotes_gpc and, if it is turned on, pass all input through PHP's stripslashes() function. Then apply addslashes() to values for use in database queries.
if (get_magic_quotes_gpc()) { $_REQUEST = array_map('stripslashes', $_REQUEST);}
SQL injection also allows malicious users to get to your database records. Always check (case-insensitive!) data that will be used in a query for the characters '",;() and for keywords like "FROM", "LIKE", and "WHERE".
Shell Command InjectionLet's assume that you have secured your user login code as detailed above. Once the user has logged in, the Flex app could for example ask for a list of files that was uploaded by the user through a variable called search. The flex side of things would be similar to the example above, so I won't repeat it. The PHP snippet could look something like this:
[viewcode] src="flexsecurity/phpdir.txt" link="no" showsyntax="no" geshi="php"[/viewcode]This PHP code is not secure. The $_REQUEST variable is assigned without any validation. A malicious user might append something like ";rm -rf *" and delete your web site folder. You must ensure that the user input is valid and nothing more than what is expected. Do not only use Flex-based validation for this: there are many HTTP monitors and SWF decompilers readily available to hackers that permit modifying your Flex file. You need to add PHP code to ensure that the information the user provides is valid, like so:
[viewcode] src="flexsecurity/phpsecdir.txt" link="no" showsyntax="no" geshi="php"[/viewcode]
escapeshellcmd() escapes any characters in a string that might be used to trick a shell command into executing arbitrary commands.
OK, that concludes the first part of this article. In part two, we'll go into some other potential security holes like error reporting and safe mode.

热AI工具

Undresser.AI Undress
人工智能驱动的应用程序,用于创建逼真的裸体照片

AI Clothes Remover
用于从照片中去除衣服的在线人工智能工具。

Undress AI Tool
免费脱衣服图片

Clothoff.io
AI脱衣机

AI Hentai Generator
免费生成ai无尽的。

热门文章

热工具

记事本++7.3.1
好用且免费的代码编辑器

SublimeText3汉化版
中文版,非常好用

禅工作室 13.0.1
功能强大的PHP集成开发环境

Dreamweaver CS6
视觉化网页开发工具

SublimeText3 Mac版
神级代码编辑软件(SublimeText3)

热门话题
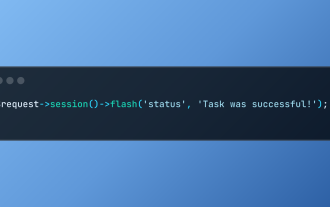 在Laravel中使用Flash会话数据
Mar 12, 2025 pm 05:08 PM
在Laravel中使用Flash会话数据
Mar 12, 2025 pm 05:08 PM
Laravel使用其直观的闪存方法简化了处理临时会话数据。这非常适合在您的应用程序中显示简短的消息,警报或通知。 默认情况下,数据仅针对后续请求: $请求 -
 php中的卷曲:如何在REST API中使用PHP卷曲扩展
Mar 14, 2025 am 11:42 AM
php中的卷曲:如何在REST API中使用PHP卷曲扩展
Mar 14, 2025 am 11:42 AM
PHP客户端URL(curl)扩展是开发人员的强大工具,可以与远程服务器和REST API无缝交互。通过利用Libcurl(备受尊敬的多协议文件传输库),PHP curl促进了有效的执行
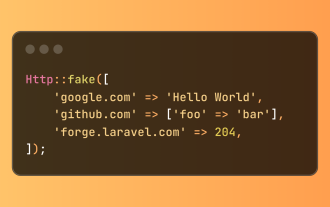 简化的HTTP响应在Laravel测试中模拟了
Mar 12, 2025 pm 05:09 PM
简化的HTTP响应在Laravel测试中模拟了
Mar 12, 2025 pm 05:09 PM
Laravel 提供简洁的 HTTP 响应模拟语法,简化了 HTTP 交互测试。这种方法显着减少了代码冗余,同时使您的测试模拟更直观。 基本实现提供了多种响应类型快捷方式: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 在Codecanyon上的12个最佳PHP聊天脚本
Mar 13, 2025 pm 12:08 PM
在Codecanyon上的12个最佳PHP聊天脚本
Mar 13, 2025 pm 12:08 PM
您是否想为客户最紧迫的问题提供实时的即时解决方案? 实时聊天使您可以与客户进行实时对话,并立即解决他们的问题。它允许您为您的自定义提供更快的服务
 解释PHP中晚期静态结合的概念。
Mar 21, 2025 pm 01:33 PM
解释PHP中晚期静态结合的概念。
Mar 21, 2025 pm 01:33 PM
文章讨论了PHP 5.3中引入的PHP中的晚期静态结合(LSB),从而允许静态方法的运行时分辨率调用以获得更灵活的继承。 LSB的实用应用和潜在的触摸
 在PHP API中说明JSON Web令牌(JWT)及其用例。
Apr 05, 2025 am 12:04 AM
在PHP API中说明JSON Web令牌(JWT)及其用例。
Apr 05, 2025 am 12:04 AM
JWT是一种基于JSON的开放标准,用于在各方之间安全地传输信息,主要用于身份验证和信息交换。1.JWT由Header、Payload和Signature三部分组成。2.JWT的工作原理包括生成JWT、验证JWT和解析Payload三个步骤。3.在PHP中使用JWT进行身份验证时,可以生成和验证JWT,并在高级用法中包含用户角色和权限信息。4.常见错误包括签名验证失败、令牌过期和Payload过大,调试技巧包括使用调试工具和日志记录。5.性能优化和最佳实践包括使用合适的签名算法、合理设置有效期、








